The Cost of Skimping on Security in 2022
From 2020 to 2021, the number of ransomware attacks on organizations increased by 78% and more than 10% of those attacks resulted in ransoms of $1 million or higher. According to the Sophos State of Ransomware 2022 report, ransomware attacks take an average of one month to fully recover from and frequently result in downtime and loss of revenue, the impact of which leads to an average recovery cost of $1.4 million. That’s about 640 vacations to Disney World. The cost of skimping on security is great.
While you could take your entire team to Disney World for a week, possibly even a few times over, a better idea might be to invest in preventing a security breach in the first place. Be it ransomware, a phishing attack, or an insider threat, proactive threat and risk prevention takes dedicated time, well-trained people, and cutting-edge technology, so it is no surprise that it can be confusing and costly. As we’ve already seen, it can be even more costly to ignore those risks.
Keeping Up with Technology
It took 2 million years for humans to progress from the first tools to discovering fire, yet it only took 130 years to go from the telegraph to the internet and another 33 years to get to the iPhone. Technology now changes at a blistering pace and, alongside that thrives the unfortunately fruitful business of cybercrime. One of the most critical factors in combating this is having, understanding, and fully utilizing the latest technology. Based on Gartner’s 2022 report of Top Strategic Trends, some of the newest technologies that will impact the cybersecurity field include:
- Cybersecurity Mesh: A scalable, integrated architecture that enables security tools to work cooperatively throughout an environment
- Autonomic Systems: Self-managing systems that take in information from the network to modify algorithms without manual updates, allowing for rapid changes and scalability
Source: Gartner
Partnering with the Experts

Whether you are intimately familiar with the concepts presented here or they sound like something from the USS Enterprise, partnering with experts is what will give you an advantage over bad actors and cyber criminals. Admittedly, most organizations struggle to keep up with regular patching, let alone investing the time and resources into implementing these types of technology. While cybersecurity and understanding cyber risk are likely not your area of expertise, working with a trusted partner can ensure that your online business and IT landscape are as secure as technology and expertise allow. Having security that stands up to the worst of ransomware, hackers, and more is a must.
The criminals don’t take a break, so your security monitoring can’t either, which is why it is critical to have both the technology to meet the needs of today’s risks as well as the people to understand, implement, and manage that technology to its fullest potential. Aunalytics has you covered. With expert toolsets and talent, your business can depend on us to have highly trained professionals and the newest technology and information to protect your business in the ongoing threat landscape.
Don’t Let Your Sensitive Data Go Unprotected
Every business has sensitive data that should not be shared with the world at large. Credit card information, personal details, company records—all of this data can be exposed or stolen and ransomed via a single bad actor.
Is Your Data Safe?
Everyone from banks and credit unions to government agencies and utility companies need one basic thing that can stop bad actors: good data security. With hackers and ransomware encroaching on your network, it’s more important than ever before that you have proactive data protection in place.
Good data security includes 24/7/365 monitoring of your network, constant threat and vulnerability scanning, a functioning Security Operations Center (SOC) and more. The problem? It’s hard to find talent to maintain a functional SOC, and when you do find talent your mid-market business may not be able to compete with offers from large enterprises.
While finding, paying, and retaining high quality talent is hard, partnering is not. A side-by-side approach with a knowledgeable partner allows you to actively react to the ever-changing digital landscape—not after your company’s security has been left behind and open for bad actors.
How Can You Protect Your Data?
Many security tools are made for experts—security engineers, network engineers, and others with specific technical expertise. Because the security landscape keeps changing, as bad actors evolve techniques and new threats are constantly emerging, security requires full time dedication to researching and staying up to date with threats, new prevention measures and remediation best practices. Most IT departments do not have time for the research and adaption that security requires. If you don’t have a team that can constantly update your security to provide your company with the best security possible, your security posture will begin to sag. A sagging posture isn’t good for any industry or company—and it needs to be fixed immediately.
By hiring a trusted partner, you can ensure that your sensitive data is secure. Having security that stands up to the worst of ransomware, hackers, and more is a must. An SOC takes care of things for you.
If your company doesn’t have an SOC, it is falling behind. Out of date security means injury to your network becomes more and more likely, and a security event can cause you to lose clients and prospects, large sums of money, and even tarnish your company’s reputation.
Partnering Up
You should already have an internal IT team. Aunalytics’ SOC isn’t meant to replace your IT team, but to supplement and support your team’s security initiatives. An SOC can stop threats before they enter your network and cause chaos, keeping your data out of the hands of bad actors everywhere.
When you need to protect your data, Aunalytics has you covered. With expert toolsets and talent, your business can depend on us to have highly trained experts and the newest technology and information to protect your business in the ongoing threat landscape.
See Yourself in Cyber—How Individuals Can Reduce Security Risk
It seems like just yesterday our biggest security risk was a ‘long lost relative’ claiming we had millions of dollars waiting for us if only we would send them a little money up front. The world and technology have come a long way since then, and not always for the better. Now we are inundated with spam in the form of calls, texts, emails, and every other form of communication in existence—all alongside our actual conversations. Your grandma might message you on Facebook to ask for your help and it turns into requiring a trip to Walmart to buy $500 in Apple gift cards. Your CEO might text you with an urgent request when they’ve never texted you before. With this constant barrage of threats that continue to get more and more believable, is it even possible to be safe online? It most certainly is, but it requires vigilance and a keen, informed eye.

October is Cybersecurity Awareness Month in the US and this year’s theme is ‘See Yourself in Cyber’. Whether you’re the head of IT, a bank teller, a homemaker, or anything in between, you’re at risk of a cybersecurity attack. However, the industries experiencing the highest number of incidents are finance, healthcare, and public administration. As scammers, hackers, and generally ‘bad actors’ hone their craft, we also need to sharpen our detective skills. It’s an unfortunate truth, but we need to learn how to spot the red flags because it’s expected that, by 2025, there will be an average of 10 devices per person connected to the internet globally. All of which become a playground for cybercriminals if the devices aren’t well guarded by technology—and you.
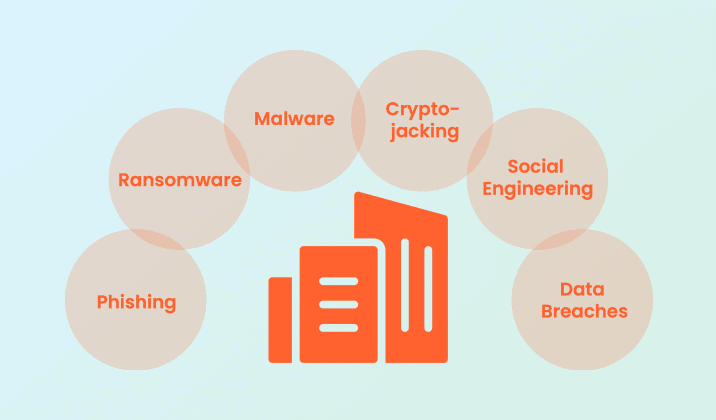
Types of Threats
There are as many reasons bad actors attack as there are ways they do it. Understanding the most common methods will help you better avoid them in the wild. Here are some of the most widespread attacks you might see:
- Phishing: When a bad actor sends an email that appears to be from a reputable source or someone you are likely to trust in the hopes that you will open an infected attachment or follow a malicious link. This could allow them access to your system or persuade you to divulge personal information, such as passwords or credit card information.
- Spear Phishing: When a bad actor sends a phishing attack specifically targeting you. Typically, it will include information they’ve learned about you from social media or other online public forums.
- Smishing: This is phishing in the form of a text message.
- Vishing: This is phishing in the form of a phone call.
Spotting the Red Flags
For these types of threats, you’ll need to be able to identify something out of place to make you pause before taking any harmful actions. However, this is where vigilance is critical because these red flags are becoming increasingly more difficult to spot. Below you will find guidance on where you are most likely to spot a threat:
- Email is the most likely path a scammer will take. When identified separately, these signs may not seem concerning, but when combined, they are a sure sign of a phishing attack.
- Does the subject line or content of the email seem alarming or urgent?
- Is the email from someone unexpected or unknown?
- Is the ‘reply-to’ address different from the ‘from’ address?
- Did the email come in at an unusual time or day, such as in the middle of the night or on a weekend?
- Are there grammar or spelling mistakes?
- Does the wording seem unnatural?
- Are there unexpected or suspicious links or attachments?
- Are they offering you money or gift cards in exchange for an action?
- Is the email unexpected or out of place?
- Text messages may come in a different format, but they can still open you to the same security risks. Many of the red flags above still apply, but these are the most common examples in smishing.
- Is the sender claiming to be an executive at your company with an urgent need?
- If you know the sender, is the text from the number you have for them?
- Are you being asked personal information?
- Are you being asked to follow a link?
- Phone call scams commonly prey on the elderly and are more common outside of the workplace. Common signs to look for in vishing are:
- Is the call unexpected?
- Does the caller request access to your device to solve an issue?
- Does the caller threaten legal action or claim to be from a governmental body such as the IRS?
- Does the caller claim you have won money or a prize?
- Does the caller request payment in the form of gift cards or money orders?
Protecting Yourself
This feels like a lot of effort; what’s really the worst that can happen if you fall for one of these scams? If you click on a malicious link or download an infected attachment, you leave the door wide open for a hacker to access not only your device, but your entire network of devices and data. If they are able to access your personal information, they could potentially access your bank account, credit card information, or other private accounts. Shockingly, 88% of data breaches are caused by employee mistakes. Here are some steps you can take to ensure you aren’t part of that 88%:
- If an email comes from someone you work with, but you are noticing red flags, especially links or attachments, contact the person directly to verify they actually sent it.
- If there are links in the email, hover over them to ensure they match what is being displayed.
- Ensure links point to a trustworthy site. For example, you might receive an email from Microsoft asking you to reset your Outlook password, but when you hover over the link, it shows http://www.microsoftt.com/. Notice the misspelling in Microsoft.
- If you are unsure of a link, navigate to the website through your browser rather than clicking the link.
- If you receive an attachment that you didn’t expect, such as a financial statement when you don’t work in finance or a UPS shipping confirmation when you didn’t order anything, don’t open it until you can confirm its validity.
- Always remember, it is truly better safe than sorry when it comes to suspicious links or attachments.
This is just a small window into an ever-changing landscape of security threats. It might feel impossible to keep up as threats evolve, but there are ways to stay informed and vigilant for both you and your company. Through its Secure Managed Services Solution, Aunalytics provides the tools and talent you need to stay protect from outside threats, include a streamlined training platform to ensure you and your team can stay up-to-date with current threats and reduce security risk. When you are able to ‘See Yourself in Cyber’, you become critical in fighting against bad actors and the cyber threats they pose.
Don't Let Your Data Work Against You—Your Organization Needs a Single Source of Truth
As the business landscape continues to evolve and become more data-driven every day, organizations need to go through an intense digital transformation to remain competitive. The need to leverage data to maximize business opportunities and revenue is evident. While at one time technologies were built solely for enterprises, now most mid-sized businesses are beginning to invest in data analytics solutions. But before successfully deploying an analytics solution, there might be a major organizational problem to deal with—your dirty data might be getting in the way of getting accurate analytics. What you need is a single source of truth.
Gain a Complete, Accurate Picture of Customers
Let’s pretend you have a client named Emily Miller. Your marketing department has Emily logged in their CRM, while the sales team has their information in a spreadsheet that they update daily. The service department logs their tickets and complaints in their own solution, while accounting has Emily’s invoices in yet another system. We’re talking about one person, but there are multiple versions of Emily’s data across your organization, siloed in different departments. While we know Emily’s name, her interactions with your organization and all the data related to her is scattered across your organization. Departments have partial information that is specific to Emily, but it might be inconsistent business unit to business unit. This means that no one can see the complete picture of who this customer is to your company.
If analytics is based upon data from one business unit, it will undoubtedly result in inaccurate or incomplete insights. If you switch analytics to be based upon a different data source or aggregate multiple data sources with conflicting information, you still get inaccurate analytical results. Basing your organization’s analytics only on a part of a client’s data has a negative impact on your organization’s goals. A single source of truth ensures you have a full, 360-degree picture of your clients and leads to dependable, daily analytics you can trust.
Utilize a Solution That Ensures Data Accuracy
An analytics platform such as Daybreak with built-in data integration and cleansing, or a data accuracy solution such as Aunsight Golden Record enables your organization to integrate and wrangle siloed data from disparate sources to a cleaned and accurate single source of truth. Matching and merging dirty data into a single source of information will result in you receiving consistent, accurate data from across your organization. With clean, accurate data for your reporting you can be prepared for better decision-making, allowing you to progress towards your business goals faster than ever before.
If your departments are using different data sources, using that information for client analytics is counterproductive. This situation is akin to your hands working separately from each other and adversely affecting your end goals. You need to bring your company-wide data together and combine it into a single source of truth. Having clean information with input from all your departments going into a single analytics solution sets you up for actionable insights that work along with you—not against you.
Government Agencies Need Proactive Security Plans in Place to Defend Against Ransomware
Cyberattacks are increasing across all industries, but for state and local governments and government agencies, the threat is imminent. Attackers are becoming more sophisticated and use a wide variety of tactics to infiltrate organizations. Now, more than ever, a proactive security posture is imperative to avoid the loss of sensitive data and costly downtime.
The Stats
With 58% of local and state governments reporting a ransomware attack within the last year, government agencies became one of the most heavily affected groups – second only to academia – in 2021, according to the FBI.
It’s not cheap when government offices fall victim to a ransomware attack. Often agencies are attacked by complex cyberattacks that are difficult to detect and even more difficult to remove while keeping your data safe and your services uninterrupted.
Ransomware isn’t uncommon, but that doesn’t stop your agency from going down for an extended period of time—downtime that cost local and state government entities an estimated $623,700,000 in 2021, reports EMSISOFT in an August, 2022 article.
The Solution
A Security Operations Center (SOC) is becoming a necessity for government agencies of all levels. With the government sector being a prime target for hackers and cyberattacks, it’s imperative that proactive security is in place to protect your confidential data. With a continually increasing threat landscape, having security that can stand up to the worst of bad actors is a must. An SOC takes care of things for you.
Why an SOC? An SOC can answer threats before they slip into your network and servers—before important data has been stolen by the bad actor. Does your organization have an SOC? If not, your agency is falling behind and your security is not up to date, meaning it may not protect you from all cyberattacks that will try to injure your network.
SOCs can be expensive and complex to build, and even harder to fill with talent. Even with the short supply of talented security engineers, most entities cannot afford to compete with the money big names like Microsoft, Google, and Facebook offer, but it doesn’t mean you should go without an SOC.
Getting Help
FedRAMP certification is a long, difficult process, upon which a service provider becomes an expert in providing a secure platform to manage credentials, vendors, workforce, and more. A FedRAMP certified company can best protect your data and uphold your privacy, security, and confidentiality.
Aunalytics is proud to be one of a select few to be FedRAMP ready certified in the Midwest, meaning we have achieved compliance to meet FedRAMP security standards.
With the security standards that FedRAMP certification requires—and a proven history of working with local governments throughout the Midwest – we have tools and talent to protect your data with the most up to date security practices with our Advanced Security service. With an ever-changing landscape that always includes threats, a trustworthy security partner can help keep your data safe, using 24/7/365 threat and vulnerability scanning, allowing us to find and stop bad actors before they ever access your network.
Workstation and Server Patching Allows for Better Security, Helps Curb Cyberattacks

It’s easy for something—or someone—to slip through the cracks in your security. As a result, this leaves your organization vulnerable to attack without the right security patches. In a world where ransomware costs a company an average of $4.54 million per attack—before the cost of paying the ransom—patches are essential to the security of any organization, from midsized companies to large enterprises. Undoubtedly, patches give your network the security it needs most.
Why patch?
Patching ensures your servers and workstations have thorough protection from the latest security threats—stopping threats as they emerge. Therefore, threats that would have taken out your company for an extended period are no longer a concern with proper security patching.
But patching can be difficult to manage, keep track of, and update promptly. Setting up and coordinating manual patching across an organization can feel like a nightmare, taking days to organize, schedule, and execute across your entire company.
Crucial for Company Security
Workstation and server patching is crucial, stopping devastating malware attacks, like WannaCry, in their tracks. McKinsey cites good patch management as a top proactive maintenance measure that can help your organization prevent cyberattacks.
Knowing the priority level for patch installment can be confusing, leading to poor patch management. Therefore, enlisting the help of a partner to employ security patching best-practices can be a boon to many organizations. Since Aunalytics is well-versed on patching, patch installments are timed to avoid as many bugs as possible, and patches are prioritized in order of importance. Patching keeps those who would hurt your business at arm’s length—and with Aunalytics, you don’t have to worry about patching your workstations and servers yourself, you will have a trusted partner to back you up.
We believe security is so important that we embed it into our Advanced Security offering, helping your business thrive at no additional cost to you. Gain peace of mind and eliminate technical worries with Aunalytics.
Enterprise Cloud Solutions Allow Businesses to Scale and Thrive

Paul Delory, Senior Director Analyst at Gartner says, “Cloud adoption accelerated rapidly during the pandemic and will accelerate further in the years to come.” There are several new advancements in the global IT infrastructure that have made deployment easier, which enables use cases which were previously considered to be unfeasible.
To get the most out of cloud storage, however, you need to find a cloud computing solution that fits your company’s needs. An enterprise cloud solution is a natural progression for any organization that has outgrown an onsite, physical server. A switch to a cloud computing solution can be compared to switching from everyone in an organization from owning a basic car to everyone in your organization carpooling in an efficient high-performance vehicle. Everyone gets to pool the resource and share it, but can also maintain their individuality.
A customer does not need to buy a physical or cloud server—instead they buy CPU, RAM, and storage components to satisfy their data and computational needs. These solutions often have scalability factored in, and, as you have greater needs as you grow, cloud providers are able to open more CPU, RAM, and storage as needed. For any organization, this option is significantly more feasible than having to buy double or triple the CPU and RAM for a physical server that they have on site. Our Enterprise Cloud offers server space in a shared environment that partitions a particular user’s CPU and RAM needs, alongside other user’s CPU and RAM needs, into a single, larger, combined CPU provisioning—and a single, larger, combined RAM bucket that are both Enterprise-level.
Aunalytics has high performance infrastructure solutions that provide scalable platforms for all your needs—including hosting servers, data, and applications at any performance level you’ll need. With this elastic infrastructure, we can support your ever-expanding needs and ensure your business is able to leverage the most robust cloud computing environment. Our hosting solutions are backed by our expertise in data, analytics, machine learning, and more.
To ensure the highest level of reliability, we host our Enterprise Cloud solution through multiple geographically diverse company-owned data centers, which provides you with a highly redundant and scalable platform. This cloud solution is intended to keep your data extremely safe and accessible and is scalable to handle any level of I/O intensive workloads.
Access to a strong cloud computing and storage solutions enable you to experience true efficiency as you manage, run, and secure applications across multiple devices. To increase your business’s agility, and meet your needs and your clients’ expectations, consider using a cloud computing solution and leverage the benefits of a consistent infrastructure with the ability to dynamically adjust to your requirements.
Focusing on Business Outcomes Leads to Analytics Success
Most organizations today realize that their everyday data holds value, yet is a resource that often remains untapped. Community banks and credit unions in particular are beginning to see the necessity of investing in these initiatives to compete with large banks and fintechs. However, despite investment in technology solutions that enable advanced analytics, many organizations still fail to succeed in realizing the value. According to Gartner, through 2022, only 20% of analytic insights will actually deliver business outcomes. Why do so many of these projects fail? For many organizations, they lack a clear vision of success. Their success measures should not be to simply build a data warehouse or hire a data analyst. The success measures should center around specific business outcomes.
In the video clip below, Rich Carlton, President and Chief Revenue Officer at Aunalytics, talks about how the right combination of technology, data and analytics talent, and a focus on achieving specific business objectives leads to analytics success.
Aunalytics provides an end-to-end data and analytics solution, including the technology, talent and expertise to help organizations focus on achieving actionable business outcomes. This insights-as-a-service model removes the pressure of building up an analytics infrastructure so businesses can focus their energies on realizing the value in their data much sooner. To learn more about how Aunalytics empowers community banks and credit unions with the ability to turn their data into actionable insights, watch our webinar, “Enhance Customer Experience and Increase Market Share with AI-Driven Personalized Interactions.”
Backup vs Disaster Recovery: What’s the Difference?
Your data is vital for your business to function. Often, companies are not completely confident in what should be a part of their Business Continuity Plan (BCP), and do not understand that they need both data backup and disaster recovery to re-operationalize the business to be covered for outages and disasters.
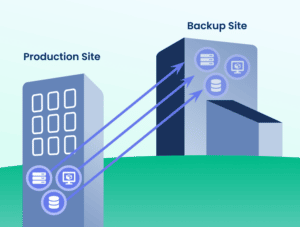
Backup
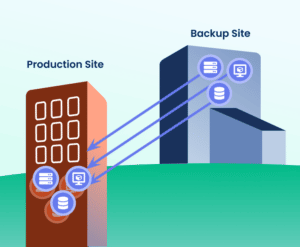
Disaster Recovery
Disaster recovery services are designed to bring a business back online after a failure at the primary business site. Disaster recovery includes steps to operationalize the data back-ups, and bring back online networks and systems should an attack or outage occur. With a disaster recovery solution in place your organization’s data and the functioning of your IT systems are restored. An all-encompassing Disaster Recovery plan restores business functions and minimizes losses and downtimes. It includes server level and site level restoration. You may have to invest in an entire secondary IT infrastructure unless you have a Disaster Recovery as a Service (DRaaS) provider.
Business Continuity Plan
A Business Continuity Plan should include both backup procedures so that you protect your business from data loss, and disaster recovery plans to restore networks, systems and data after failure at your primary business site. For IT resiliency, your plan should include: active monitoring and assessment of IT hazards; resiliency risk assessment including potential consequences; risk and mitigation strategies; understanding of business relevance of the assets to understand business drivers and classify assets in terms of business criticality; and setting IT resilience priorities. Recovery plans should be drilled and tested regularly.
Aunalytics Backup and Disaster Recovery services will give your organization the peace of mind that, no matter what circumstances come, a trusted partner will have your back. You will not have to worry about data loss or theft, as backing up your on-premises data to the cloud will allow your company to have a business continuity plan in place to save critical business information, and you will have experts on hand to help your IT team restore networks, systems and data after a disaster.
Timing is Everything in Delivering Data-Driven Insights for Bankers
Many banks and credit unions have set their sights upon initiatives that would allow their teams to make informed, data-driven decisions to improve their business. But when it comes to delivering data-driven insights, timing is everything. Currently, too many mid-sized credit unions and banks rely upon reporting modules from their banking cores for trying to understand business performance and making business decisions. The problem with doing this is two-fold.
First, core reporting only shows you what happened in the past. It does not give you predictive insights for acting now or in the future. As we know, market conditions can rapidly change. Looking back on what worked for your institution three months ago may be informative on past performance, but it is of limited value in deciding what to do next. Your analysis is limited to a review of the past, and then guesswork for what to do today. This is a business review, not data analytics.
Second, by the time that most financial institutions get their core reports, it is months later. This means that if you are basing decision-making on analysis of the core reports, you are making decisions based upon stale data. As we know, market conditions can rapidly change. For example, if you are looking back 3-6 months, you may likely see strong mortgage lending performance. But as we know, with climbing interest rates and inflation, mortgages are not the hot product that they were six months ago. If you decided to double-down on marketing and sales campaigns for achieving new mortgage loans, you would not have the return on this investment that you might have had six months ago. The core report data is stale and does not reflect the market changes.
Timing is Crucial

For example, when a member changes jobs you have a window of opportunity to market an IRA product before the member likely settles into a new 401(k). If you market the IRA to the member three months later, she likely has rolled over into the new 401(k) and you missed your opportunity. Yet if you had a data analytics solution that provided daily insights, such as a change in the income stream pattern by amount or timing of payroll deposits, this could alert you to a change in employment status as it is happening. This gives your team the ability to sell an investment product when the opportunity is ripe.
Delivering Fresh Data-Driven Insights
Only predictive data analytics can deliver daily insights at scale for all of your customers or members. By detecting trends and patterns revealing growth drivers through predictive analytics, your team can be nimble and positioned for informed decision-making. This leads to doing more of what is working and less of what is not effective in growing operating income and customer loyalty.