Security Maturity Improvement is Imperative as Cyberattack Risks Remain High
Security Maturity Improvement is Imperative as Cyberattack Risks Remain High
While advancing technology offers significant benefits, it has also made it easier for those who seek to gain an advantage by exploiting others. An attack can be devastating for any business and impact it for many years to come—today’s organizations need to move toward security maturity by utilizing multiple lines of defense against cybercrime.
When Was the Last Time You Checked on Your Internet Security?
Internet security—a combination of security measures put into place to protect any transaction or activity made over the internet—is one of the most necessary forms of security your business could possibly have.
Everything we do, every day, is virtually always online—even though we sit next to Deborah, we usually send her files through a document sharing program like SharePoint or Google Docs. We don’t walk over with a paper file and hand it to her often, if ever. When thinking of our daily interactions with the internet in corporate environments, it becomes more and more startling that many of us are not aware what our role in our company’s corporate security actually is. Some think it’s remembering to change your password, while others know there are specific steps you can take to better secure your network from the malicious creepy crawlies.
They're Everywhere
Security threats are as widely varied as the content on the internet and can include everything from the well-known malware and phishing to Wi-Fi threats, computer worms, and botnets.
How many people do you know that take their work devices with them to coffee shops for a change of pace? As safe and normal as this may seem, there are multiple kinds of Wi-Fi threats that can piggyback onto public Wi-Fi and open networks. The three most common types of Wi-Fi threats are Man-in-the-Middle (MitM), Rogue Networks, and Packet Sniffing.

Let’s break this down a little bit:
- Man-in-the-Middle (MitM) attacks are generally the most common type of Wi-Fi threat. In its most basic form, a MitM attack is when a bad actor is able to intercept and read messages between users who believe they are only speaking to each other privately, essentially eavesdropping on their conversation and any confidential information that is being shared.
- Rogue Networks are fake Wi-Fi networks that attackers set up to confuse users into giving hackers access to their devices. Rogue networks can easily masquerade as trusted networks, especially those at locations like your favorite bookstore or coffee shop. If you see a guest network, only use it if the network is secured and you need a password to log into the network. This can help ensure your computer and other tech is better protected and is less likely to end up on a rogue network.
- Packet Sniffing, sometimes known as Packet Analyzers, can monitor traffic on a network. This malicious attack can intercept data while it is being transmitted across your network and provide hackers with details on the data package’s contents. Using this method, bad actors can also introduce errors that can corrupt your system.
Wi-Fi threats aren’t the only internet threats to your corporate security. Botnets, a network of private computers that are infected with malicious software and often controlled by a single user, are most often used for denial-of-service (DoS) attacks, and sending out spam messages for users in your network. Similarly, a computer worm, a software that can copy itself multiple times, can spread across your network quickly, leaving mass destruction in its wake.
What Now?
With the threat of bad actors finding a hole in your network at any point in time, it’s impossible to ignore your cyber security. Risks are becoming higher as viruses and malware become increasingly complex, setting companies up for difficulties when navigating the process of recovering data, and further difficulties of finding easily obtainable cyber security insurance following a security event. Finding and utilizing a trusted partner can help you keep your network safe and consistently monitored with services like a 24/7/365 monitored Security Operations Center (SOC), help attaining industry security compliance requirements, and developing a Backup and Disaster Recovery (DR) plan for when the unexpected strikes.
Ransomware Attacks in Manufacturing Pose An Increasing Threat
Cyberattacks are a constant threat to organizations of all sizes. Manufacturing and production industries may have experienced fewer cyberattacks than other industries, but companies are still at risk from bad actors. To gain a better understanding of the current attack environment and track changes over time in ransomware trends, Aunalytics security partner Sophos commissioned an independent, vendor-agnostic survey of 5,600 IT professionals in mid-sized organizations across 31 countries. Out of all the respondents, 419 were from the manufacturing and production industry. This survey was conducted in January and early February of 2022. While it’s true cyber insurance has been playing a greater role in helping organizations improve their ability to recover from attacks, survey responses clearly indicate the rising threat ransomware poses to the manufacturing industry.
Cyberattacks Are Up From Previous Year
Ransomware attacks have increased significantly over the past year—55% of manufacturing and production organizations surveyed were hit by an attack in 2021, up 36% from 2020. Bad actors are now considerably more capable of attacking businesses and executing harmful tactics at scale. The Ransomware-as-a-Service model is one cause of this year’s increased attacks, as the required skill level for bad actors to hamper the day-to-day operations of an organization has gone down significantly.
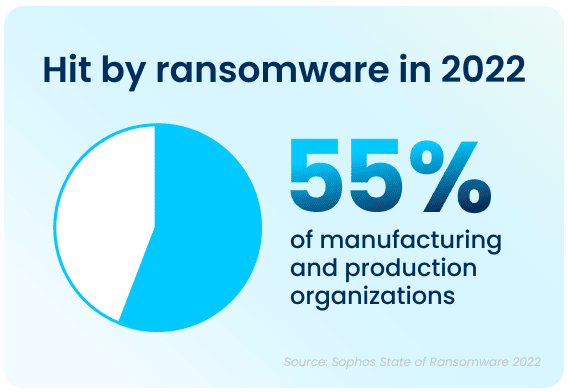
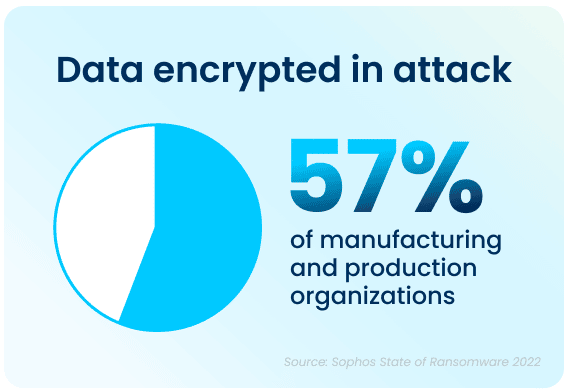
Apart from the rising prevalence of these attacks, the sheer complexity of each attack is also on an upwards trajectory. While the manufacturing and production industry reported the lowest rate of ransomware attacks, but, with over half of all respondents in all surveyed industries reporting that their company was been injured by bad actors, the reality is that every organization is at high risk of attack. In 2021, 57% of attacks in the manufacturing and production industry resulted in important data being encrypted. Additionally, 59% percent of organizations who experienced cyberattacks saw the complexity of the attacks increase, while 61% saw an increase in the overall volume of cyberattacks.
Data Recovery Rates Are Improving
While the increase in cyberattacks paints a bleak picture, there is a silver lining to this dark cloud. 96% of manufacturing and production organizations were able to get some of their encrypted data back. The top method used to restore data was backups, which were used by 58% of organizations whose data was encrypted in an attack. Unfortunately, despite the utilization of backups, a third of the effected organizations still had to pay a ransom to ensure that more their data was restored.
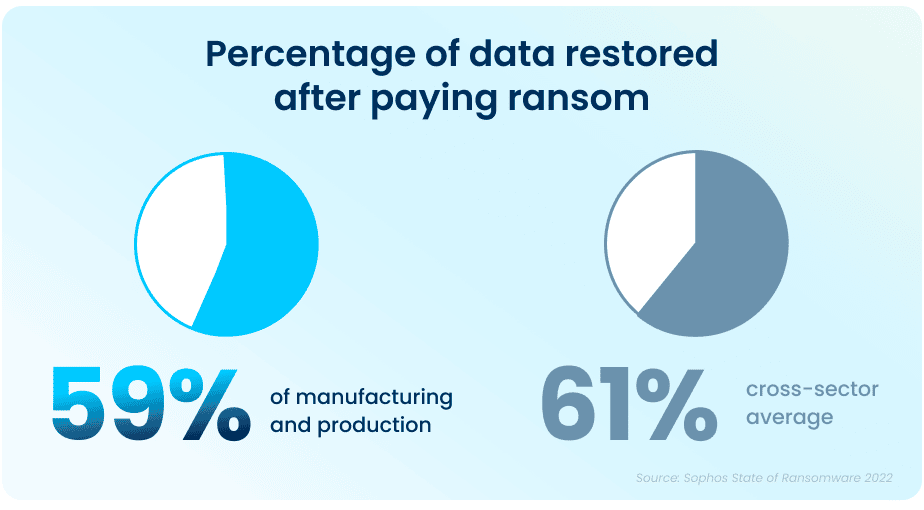
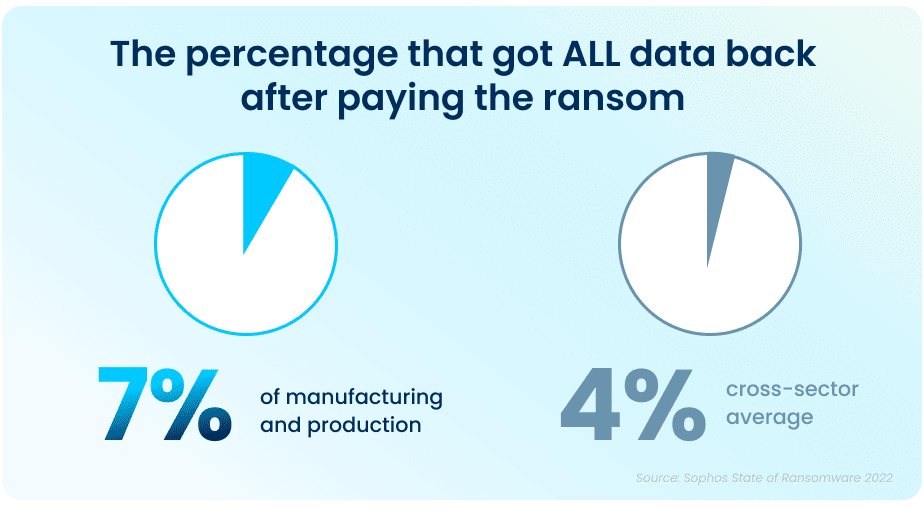
Unfortunately, while paying a ransom typically allows organizations to get some data back, it is proving to be less effective than in years past. On average, in 2021, organizations that paid a ransom only got back 59% of their data, and only 7% of those that paid the ransom got ALL of their data back. This highlights the importance of employing multiple methods to restore data—utilizing backups in particular can improve the speed of recovery and increase the amount of data that can be recovered in the event of an attack.
Ransom Payments Have Increased
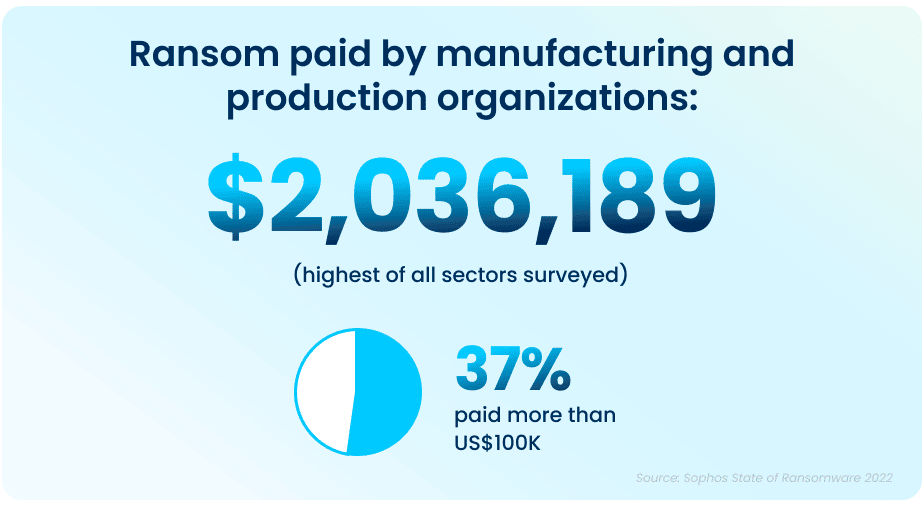
The average ransom pay-out has seen an exponential increase from what was reported in 2020 data, rising from an average of $147K (USD) to a jaw-dropping $2,036,189 (USD) in 2021.
Ransomware Has a Massive Impact on a Company’s Financial Status and Operational Capacity
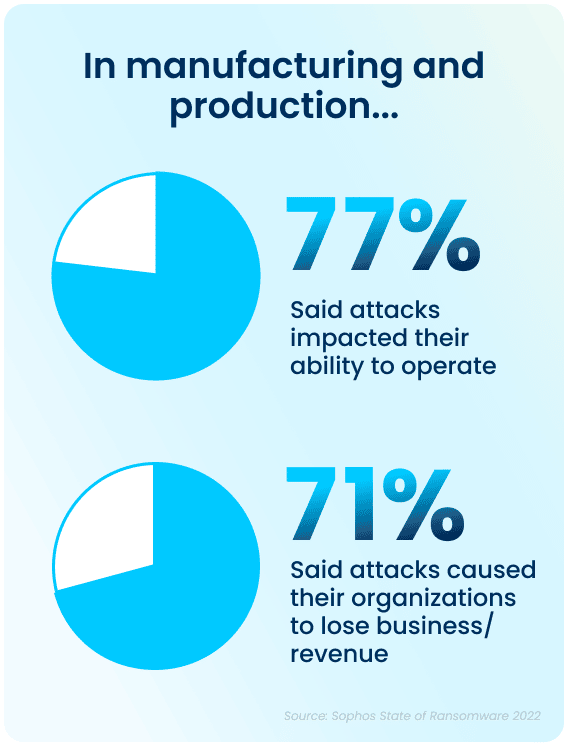
Even when some of the encrypted data is restored after a cyber-attack, there are additional costs in the form of lost productivity and a decline in operational capacity, which can have a considerable impact on your company. Of those hit by ransomware last year, 77% said their most significant attack impacted their ability to operate, while 71% said it caused them to lose business and/or revenue. The average cost to remediate an attack in 2021 was $1.23M (USD), down from $1.52M (USD) in 2020. This was due in part to cyber insurance providers being able to better guide victims through an effective response more rapidly.
Although there have been improvements in total recovery time over the years, it still took, on average, one week for manufacturing and production organizations to fully recover from the most significant attacks.
Despite the huge economic costs of ransomware attacks, many organizations are continuing to put their faith in defenses that don’t actually prevent ransomware—only more quickly mitigate its effects. Most of the organizations in the survey who weren’t hit by ransomware in the past year and didn’t expect to be hit in the future cited backups and cyber insurance as reasons why they don’t anticipate an attack. It’s important to note that neither of these elements can actually prevent cyber-attacks.
Simply having security mitigation resources in place does not mean that they will be effective against malicious attacks. Despite having ample resources—in both personnel and technology—organizations will not achieve a high return on investment without a combination of the right technology and expertise to use the technology effectively.
Cyber Insurance Drives Changes to Cyber Defenses
Thankfully, organizations do not have to shoulder the burden of ransomware costs all on their own. The survey found that three out of four manufacturing and production organizations had insurance against ransomware attacks. Organizations that had been previously hit by ransomware attacks in the past were much more likely to have cyber insurance coverage against ransomware. However, many respondents indicated that securing coverage has changed or gotten more difficult to obtain in the past year:
- 56% said the level of cybersecurity they need to qualify is now higher
- 53% said policies are now more complex
- 42% said it is more expensive
- 35% said fewer companies offer cyber insurance
- 30% said the process takes longer
As a result, 97% of organizations that have cyber insurance have made changes to their cyber defenses to improve their cyber insurance position. 70% have implemented new technologies and services, while 63% have increased staff training and educational activities, and 59% have changed processes and behaviors.
But It Doesn’t End There
The State of Ransomware 2022 survey by Sophos has revealed that ransomware continues to be an imminent threat for the manufacturing and production industry. For many, choosing an experienced partner with expertise in cybersecurity not only improves their chances of getting approved for the right amount of cyber insurance coverage, but can also ensure that companies see an higher return on investment and improved ability to both prevent and mitigate attacks in the future.
Catalyst University 2023
Catalyst University 2023
Radisson Plaza Hotel, Kalamazoo, MI
Aunalytics to Attend 2023 Catalyst University
Aunalytics is excited attend Southwest Michigan First’s Catalyst University 2022 in Kalamazoo, MI. Aunalytics is participating as a speaker sponsor and is pleased to present Mitch Albom, who is a best-selling author, journalist, screenwriter, playwright, radio and television broadcaster, and musician.

Poor Document Sharing Strategies May Share Too Much Information with Bad Actors
To share documents across your organization, it may be as easy as making a single click—but that doesn’t mean they are protected from malicious actors with bad intent. One mistake and you could be leaving holes in your security fabric, allowing hackers to access your company’s shared documents.
While file storing systems are a popular and useful solution, it can be dangerous to allow everyone in your company unimpeded access to everything they contain. Important company information, and many different files, live within document sharing applications—everything from job applications and budgets to employees’ personal information—which can make them a target for hackers. Document sharing applications can be risky if your company’s security and security training are not up to speed.
How can your organization ensure shared documents remain secure?
When looking to keep your document sharing application secure there are rules you and your employees should follow to ensure quality cyber security. A few of these rules include:
1. Use a password manager
A password manager can users track a multitude of passwords, allowing for a different, complex password for each work (or personal) login and account the user maintains. Utilize this idea to organize your passwords, maintain difficult to guess passwords, and keep track of each one in a secure digital location.
2. Enable multi-factor authentication
Multi-factor Authentication (MFA) requires you to perform a secondary action to finish logging into an account. MFA sends a message to a phone, or another device, providing you with a code that is needed to successfully log into your account. Without this code, anyone who has attained access to your email account cannot succeed in logging into your company’s network, even if they change your password and attempt to log in again.
3. Be choosy
Take the time to choose who can, should, and needs access to specific files and folders. If access is not essential to someone’s job, consider limiting their access to non-relevant portions of your document sharing solution. Removing access to HR or accounting files from someone who is in marketing may be a good choice to make. If someone needs a file from a location they do not have access to, many document sharing solutions allow you to create a link that expires after a certain amount of time. This link will only allow the receiver to view the file they need access to while they need access to it. After the link expires, the receiver will no longer be able to view the file.
4. Provide regular security awareness training
Regular cyber security awareness training sessions allow your employees to learn about new security concerns, kinds of attacks, and now to keep your organization safe from bad actors. Training employees to look for the signs of phishing, malware, ransomware, hackers, and security holes helps keep document sharing applications safe and secure.
When done right, document sharing is incredibly useful to every business, and can be done successfully by putting a little bit of extra effort into your cyber security planning. An experienced security partner can help keep your business safe from outside threats, allowing you peace of mind that your important files are secure and encrypted from bad actors.
Aunalytics, a secure managed services partner, can help you with everything from managing your IT services, to functioning as your SOC, and also provides advanced security services. With a focus on helping mid-market clients, Aunalytics works with you, step-by-step, to help you succeed your security goals.
How To Improve Your Company’s Security Awareness in 2023
We’ve almost made it through 2022, and with every year that passes cyberattacks become more targeted and deceitful. If your organization does not have a Security Awareness Training program in place, you may not know there’s a lot in the digital world that can cause severe distress to you, your coworkers, and your day-to-day operations. Long gone are the days where all we had to be wary of was an email asking you to help a Nigerian prince with their boatloads of money. Technology has come a long way—and so have bad actors trying to get access to your data and disrupt your business operations. Fortunately, there are ways to mitigate these risks.

Social Engineering Attacks
Spam and phishing calls, texts, and emails are everywhere we look—or hear—and these individuals craft their messages in the most believable ways. A relative in the need of some help or your supervisor asking you to buy some gift cards are some of the most common forms the phishing and spam messages might take. The constant barrage of threats requires you to keep a vigilant and informed eye on them. Before a bad actor can get access to the entire company’s vital data, an individual working in that company usually experiences an attack. The victim could be the CTO of a company, a receptionist, or the new intern—anyone is under the risk of a social engineering attack.
Scammers, hackers, and all other types of bad actors in this era of information technology are getting smarter, and we need to pull up our socks and get informed. It’s predicted that, by 2025, there will be an average of 10 devices per person, all connected to the internet and at risk of cyberattack. These devices need to be guarded—not only by cybersecurity services, but also by individual employees.
There are several types of threats out in cyberspace that bad actors deploy to gain access to an organization’s valuable data. The most common and widespread attacks are phishing, spear phishing, vishing, and smishing. Don’t be fooled by the names— these kinds of attacks pose a great deal of trouble unless they can be spotted before they have a chance to coerce or convince someone to unknowingly hurt their organization.
Phishing happens in the form of an email with malicious links or attachments that, if clicked, could give bad actors access to your system or persuade someone to divulge personal information in the form of passwords or credit card numbers. Spear phishing is a highly targeted form of phishing, aiming to attack and exploit one specific person. Spear phishing attacks typically include personal information about you that bad actors can find on social media or other online public forums. Smishing and Vishing are also phishing but in the form of a text message or a phone call.
Employees Can Fight Back By Getting Informed
Employees will need to be able to spot certain indicators that should make them pause before making a decision that might cause a security breach. Often, something will seem out of place with a phishing message, but your employees cannot know what to look for if they aren’t trained to see signs of malicious intent. Vigilance is critical in this scenario because bad actors are making sure that these markers are very difficult to spot. The information below can help employees begin to spot red flags:
- Phishing through emails is the most common form bad actors choose to work with. The following points might not seem like much at first glance, but, if combined, these are a sure sign of a phishing attack:
- Subject lines that have a sense of heightened urgency;
- From unknown and/or unexpected email addresses;
- Different ‘reply-to’ and ‘from’ email addresses;
- Unusual days and times for the email to have been sent—like after work or extremely early on a Saturday;
- Clearly noticeable grammar and spelling mistakes;
- Unnatural wording;
- Unexpected or suspicious links or attachments; or
- An offer for a reward in the form of money or gift cards in exchange for an action that that needs to be taken.
- Text messages also open organizations and people to the same security risks as emails, even though they are a different format. In the case of smishing, most of the red flags for phishing apply, but there are a few more that individuals should take note of:
- The sender claims to be a company executive or direct report with an urgent need;
- The number is different from the number that you might have saved;
- Enquiring about personal information;
- Requesting to follow a link or send money.
- Vishing attacks, or phone call scams are very prevalent and commonly tend to prey on the elderly. These are mainly seen outside the workplace, but they do still pose a threat. The following are some common signs people need to look out for in the case of a vishing attack:
- Unexpected calls from unrecognized numbers;
- Caller requesting access to a digital device to solve an issue;
- Caller threatening legal action and claiming to be from a government body, like the IRS;
- Caller claiming you are a prize winner;
- Caller requesting money in the form of gift cards or asking for personal information like bank details and credit card numbers;
- Caller impersonating an executive, co-worker, or even a family member has found themselves in deep, generic trouble—like getting into a car accident or being arrested—necessitating immediate cash transfers, money wires, and more to get them out of trouble or harm’s way.
Organizations should put a Security Awareness Training program in place to help their employees gain knowledge and experience a behavioral transformation, which would further impact their ability to avoid causing breaches in your organization’s network. Such initiatives ensure everyone in the company is aware of the risks that exist in the digital landscape, and they make decisions that are in the best interests of the organization’s overall security. Each employee is responsible for their organization’s cybersecurity, and if they treat all the information they have access to as a section of the overall information system, the overall system will have significantly higher chances of being secure. If your organization would like to learn more about implementing a Security Awareness Training program, contact Aunalytics today.
Cyber Insurance Continues to Skyrocket—Do You Have a Security Strategy in Place?
Cyber Insurance Continues to Skyrocket—Do You Have a Documentable Security Strategy in Place to Show You’re Prepared?
Cyber risk is a growing critical concern for organizations of all sizes and public entities globally, as we continue to rely on information technology and digital devices. But in the wake of steadily rising digital threats, cyber insurance is getting increasingly expensive—and difficult—for companies to procure.