Cyber Insurance Continues to Skyrocket—Do You Have a Security Strategy in Place?
Cyber Insurance Continues to Skyrocket—Do You Have a Documentable Security Strategy in Place to Show You’re Prepared?
Cyber risk is a growing critical concern for organizations of all sizes and public entities globally, as we continue to rely on information technology and digital devices. But in the wake of steadily rising digital threats, cyber insurance is getting increasingly expensive—and difficult—for companies to procure.
Increasingly Difficult Security Requirements Complicate Cyber Insurance Renewal
Have you received a cyber insurance renewal notice with a shocking sticker price? With an ever-increasing number of security incidents involving data breaches, ransomware, phishing scams and more, the cyber insurance landscape has changed. It’s no longer possible to get premium discounts for implementing certain security controls—more is now required. And, without enhanced security measures, you may not get cyber insurance at all.
Threats evolve over time, meaning your security posture needs to evolve in order to not only remain operational, but also be compliant to qualify for most insurance policies.
Insurance companies are now requiring more precautionary measures than ever before due to the constant—and costly—increase of threats. Premiums are increasing and coverage is being denied even for companies that have no history of breaches or claims—cyber insurance renewal rates have increased by up to 200% over the past two years, even for companies who have not made any claims.
The average cost of a data breach has raised from a massive $3.86 million in 2020 to a staggering $4.24 million in 2022.
The Solution

With the risks of operating in an increasingly digital world, cyber insurance is essential for your business to function and remain protected in the event of an attack. Aunalytics’ Advanced Security experts have the talent and technology to audit your security and discuss precautionary measures an insurance company may want you to take before renewal. With a dedicated team, your business can avoid costly data breaches, ransomware, and get your security up to snuff.
Are you ready to assess your security before your company is the victim of a bad actor, costing you upward $4.24 million dollars? See if an audit by our security experts makes sense, and whether your insurance company has outright dictated (or hinted by their renewal questionnaires) new precautionary measures that they expect your enterprise to adopt to obtain coverage.
Aunalytics Brings Its Portfolio of Managed Services, Enterprise Cloud, and Data Cleansing Solutions to Taste of IT Conference in Ohio
Leading Data Management and Analytics Company to Join More Than 400 IT Professionals for a Day of Networking and Learning
South Bend, IN (November 15, 2022) – Aunalytics, a leading data management and analytics company delivering Insights-as-a-Service for mid-market businesses, will feature its managed services, enterprise cloud, and data cleansing portfolio at the Taste of IT Conference on November 16, 2022. The one-day event, which will be attended by more than 400 IT professionals, will be held at the Sinclair Conference Center in Dayton, Ohio.
Aunalytics provides IT and security expertise to mid-market businesses in the areas of financial services, healthcare, manufacturing and professional services. The company’s Secure Managed Services offering combines mission critical IT services leveraging zero-trust end-to-end security to ensure data is protected regardless of a user’s location. Aunalytics provides managed components that offer stability and security, and its next-generation managed services offering is powered by a data platform that provides data-driven IT answers and embedded security that focuses on people and access.
The full suite of managed IT and integrated security services empowers businesses with a complete, all-encompassing approach that includes 24/7/365 monitoring and management, a synchronized network security platform, workstation and server patching, internet protection, email filtering and security, Office 365 management and security, multi-factor authentication, data and device encryption management, and security awareness training.
The company delivers advanced security for defending against modern threats through a team of engineers and analysts with expert skills and toolsets and, in regulated industries, Aunalytics provides the additional technology and controls required to manage risk. Its team of experts is dedicated to analyzing ever-changing rules and regulations and helping users to create processes and policies for data protection and meet compliance requirements within those industries that are regulated.
Aunalytics’ Enterprise Cloud offering is comprised of infrastructure solutions that provide a highly redundant and scalable platform for hosting servers, data, analytics and applications at any performance level. With the Aunalytics® Cloud Storage and Compute solution, users are assured the highest levels of security, accessibility, expertise, scalability, and savings. Aunalytics’ data centers, located in Northern Indiana and Southwest Michigan, meet the most rigorous standards for security, weather protection, temperature and humidity controls, fire suppression and more.
As data continues to expand exponentially, the challenge of data cleansing is rapidly becoming more difficult, as well as expensive. Aunalytics’ Aunsight™ Golden Record turns siloed data from disparate systems into a single source of truth across the organization. Powered with data accuracy, the cloud-native platform cleanses data to reduce errors, and Golden Record as a Service matches and merges data together into a single source of accurate business information, giving users access to consistent, trusted data across the organization in real-time. With this self-service offering, users can unify all their data to ensure enterprise-wide consistency and better decision making.
“IT executives want practical, real-world knowledge about business changing technology and management solutions that are absolutely critical to drive their businesses forward,” said Robert Lizotte, Local Market Leader, Columbus Region, Aunalytics. “As digital transformation continues to be a high priority for many organizations, our portfolio of managed services, enterprise cloud, and data cleansing solutions provides the tools they need to accelerate their digital transformation journeys. We look forward to participating at a Taste of IT and demonstrating how Aunalytics can help IT professionals advance their business success.”
Tweet this: .@Aunalytics Brings Its Portfolio of Managed Services, Enterprise Cloud, and Data Cleansing Solutions to Taste of IT Conference in Ohio #ToIT22 #Datamanagement #Informationtechnology #Managedservices #Enterprisecloud #Datacleansing #Dataplatform #Dataintegration #Dataaccuracy #Digitaltransformation #ITsecurity #Securitytechnology
About Aunalytics
Aunalytics is a leading data management and analytics company delivering Insights-as-a-Service for mid-sized businesses and enterprises. Selected for the prestigious Inc. 5000 list for two consecutive years as one of the nation’s fastest growing companies, Aunalytics offers managed IT services and managed analytics services, private cloud services, and a private cloud-native data platform for data management and analytics. Aunalytics’ data management platform is built for universal data access, advanced analytics and AI – unifying distributed data silos into a single source of truth for highly accurate, actionable business information. Its DaybreakTM industry intelligent data mart combined with the power of the Aunalytics data platform provides industry-specific data models with built-in queries and AI for accurate mission-critical insights. To solve the talent gap that so many mid-sized businesses and enterprises located in secondary markets face, Aunalytics’ side-by-side digital transformation model provides the technical talent needed for data management and analytics success in addition to its innovative technologies and tools. To learn more contact us at +1 855-799-DATA or visit Aunalytics at https://www.aunalytics.com or on Twitter and LinkedIn.
PR Contact:
Denise Nelson
The Ventana Group for Aunalytics
(925) 858-5198
dnelson@theventanagroup.com
Don’t Ghost Your Network—Begin Your Security Maturity Journey
Is your security keeping up with the rapidly changing threat landscape? If not, your security is becoming more obsolete by the day—and more vulnerable to scary things like hackers and ransomware by the second. When a company is fully protected with the most up to date hardware, software, monitoring, and consistent patching it begins to reach security maturity.
Security maturity is a consistent state of awareness concerning your network security and can only be achieved when you:
- Have an SOC to monitor and remediate threats
- Have looped vulnerability management
- Employ active defense with security intelligence from multiple sources to protect applications, networks, servers and workstations
- Are willing to adapt your security environment to new and changing threats on a constant basis, and more.

Be Proactive
Instead of relying on a passive security model—or worse, waiting until after a companywide infection—take an active role in your company’s security. The main goal of security maturity is to avoid or reduce the number of security incidents haunting your network. It’s kind of like painting San Francisco’s Golden Gate Bridge. As soon as the painting crew gets from one end to the other with a fresh coat of paint, it is time to start again to repaint the bridge. Security maturity requires constant action and change as your organization adapts to protect against the latest evolving threats.
We all observed remote work access change security and IT on a mass scale in 2020, and security changes continue to become more necessary as bad actors and threats become more and more dangerous to your business as it continues to grow and change—and more dangerous for your customers to do business with you.
October WSJ headlines highlight a Chicago healthcare system, one of the largest in the U.S., being the victim of ransomware that is forcing it to shut down electronic records, systems, and cancel patient appointments. It is now working with law enforcement and outside cybersecurity experts to remediate. A security maturity journey is hard to make on your own, and a good partner can ensure you are meeting the highest security standards possible. Here at Aunalytics, we include security in everything we do because we believe it is a basic building block of IT.
Find A Trusted Security Partner
Without a secure network, you cannot even begin to consider moving further into a security maturity journey. Fortunately, a partner can give you the peace of mind that you will be working with a talented security team that is watching your network 24/7/365, helping to ensure bad actors are caught and eradicated before your company is compromised.
A standard, one size fits all security solution simply doesn’t work anymore—it often leaves cracks, holes, and even chasms for hackers and cyberattacks to slip through. You can improve your journey from cybersecurity to security maturity with a trusted partner.
Click here to learn more.
Aunalytics Highlights Security Priorities as Cybersecurity Awareness Month Concludes
Company Recommends Cybersecurity Solutions to Better Protect Organizations Against High-Risk Cyber Attacks
South Bend, IN (October 28, 2022) – Aunalytics, a leading data management and analytics company delivering managed IT and data platform services for mid-sized and enterprise businesses, today highlighted top security priorities to follow when reinforcing defensive security strategies against malicious cyber threats. The guidance is provided as Cybersecurity Awareness Month comes to a close in October, after a month of focus on the subject.
According to Check Point Research (CPR), “2022 began with a massive exploitation of one of the most serious vulnerabilities on the internet, the Apache log4j, and continued with full blown cyber warfare from the Russia-Ukraine war. The second quarter of 2022 saw an all-time peak, where global cyber-attacks increased by 32%, compared to Q2 2021. The average weekly attacks per organization worldwide reached a peak of 1.2K attacks.”
In response to the rising number of attacks, Aunalytics is providing guidance and solutions to strengthen, educate and defend business IT systems and data from attack. These include having a comprehensive Vulnerability Management (VM) solution, Security Awareness Training, and beginning a Security Maturity Journey – all backed by Aunalytics’ expert cybersecurity team.
Aunalytics cybersecurity solutions experts recommend the following:
- Vulnerability Management (VM) – Replaces manual efforts to protect the network from bad actors using high quality equipment and tools that are typically limited to enterprise organizations. Without a VM solution in place, it is exceedingly difficult to find individuals who have slipped into the network. A VM solution is overseen by security professionals and discovers devices on a network, determines if they are vulnerable and fixes any underlying issues, while concurrently protecting the network as fixes are implemented.
- Security Awareness Training – Security management and training are crucial for businesses to avoid digital disasters. Security awareness training is necessary to educate employees about the digital dangers in their environment and how to properly deal with them. Aunalytics provides expert knowledge and toolsets that employees need in order to better protect the organization.
- Security Maturity Journey – If system security is not keeping up with the rapidly changing threat landscape, it will become obsolete and more vulnerable to bad actors. Security maturity means adapting and improving security as the environment changes and grows. It means taking strategic actions like deploying active defenses with the help of security intelligence from multiple sources. Businesses can evolve from a legacy security state to security maturity with the help of a trusted partner.
The growing threat of cybercrime is a risk to any organization connected to the Internet. Attacks can arrive in forms that include phishing, spear phishing, ransomware attacks, zero-day attacks, known vulnerability exploits, sensitive data breaches, brute-force attacks and more. Secure Managed Services by Aunalytics offers peace of mind in knowing that IT environments are monitored and managed at all times with the goal of eliminating the risk of data exfiltration or infrastructure downtime.
“End-to-end protection requires actions and defenses that consider the entirety of systems and software throughout an organization. It also means educating employees so they are ‘security aware’ to help reduce the number of threats that may enter through vulnerable endpoints,” said Steven Burdick, VP, Sales, Cloud & Managed Services. “Aunalytics protects organizations on their security journey, deploying a defensive cybersecurity framework that provides the technology and expertise for better security posture.”
About Aunalytics
Aunalytics is a leading data management and analytics company delivering Insights-as-a-Service for mid-sized businesses and enterprises. Selected for the prestigious Inc. 5000 list for two consecutive years as one of the nation’s fastest growing companies, Aunalytics offers managed IT services and managed analytics services, private cloud services, and a private cloud-native data platform for data management and analytics. The platform is built for universal data access, advanced analytics and AI — unifying distributed data silos into a single source of truth for highly accurate, actionable business information. Its DaybreakTM industry intelligent data mart combined with the power of the Aunalytics data platform provides industry-specific data models with built-in queries and AI for accurate mission-critical insights. To solve the talent gap that so many mid-sized businesses and enterprises located in secondary markets face, through its side-by-side digital transformation model, Aunalytics provides the technical talent needed for data management and analytics success in addition to its innovative technologies and tools. To learn more contact us at +1 855-799-DATA or visit Aunalytics at https://www.aunalytics.com or on Twitter and LinkedIn.
PR Contact:
Denise Nelson
The Ventana Group for Aunalytics
(925) 858-5198
dnelson@theventanagroup.com
2022 Technology First Taste of IT Conference
2022 Technology First Taste of IT Conference
Sinclair Conference Center, Dayton, OH
Aunalytics to Attend Technology First's 2022 Taste of IT Conference as a Gold Sponsor
Aunalytics is proud to be a Gold Sponsor, and excited to join over 400 IT professionals at the Technology First Taste of IT Conference on in Dayton, Ohio. Aunalytics provides a wide variety of managed IT and security solutions, such as our Secure Managed Services offering which combines mission critical IT services leveraging zero trust end-to-end security to ensure people and data are protected regardless of location. In addition, our Advanced Security solution gives organizations access to cutting-edge technology and expertise of Aunalytics professionals to prevent and mitigate cyberattacks.

Ransomware Attacks Pose An Increasing Threat to Businesses of All Sizes: The State of Ransomware 2022
Cyberattacks are a constant threat to organizations of all sizes. To better understand how the current attack environment and track how ransomware trends have changed over time, Sophos commissioned an independent, vendor-agnostic survey of 5,600 IT professional in mid-sized organizations across 31 countries. This survey was conducted in January and early February 2022. The results highlighted the increasing threat that ransomware poses, and the increased role cyber insurance is playing in driving organizations to improve their cyber defenses.
Cyberattacks are up from last year
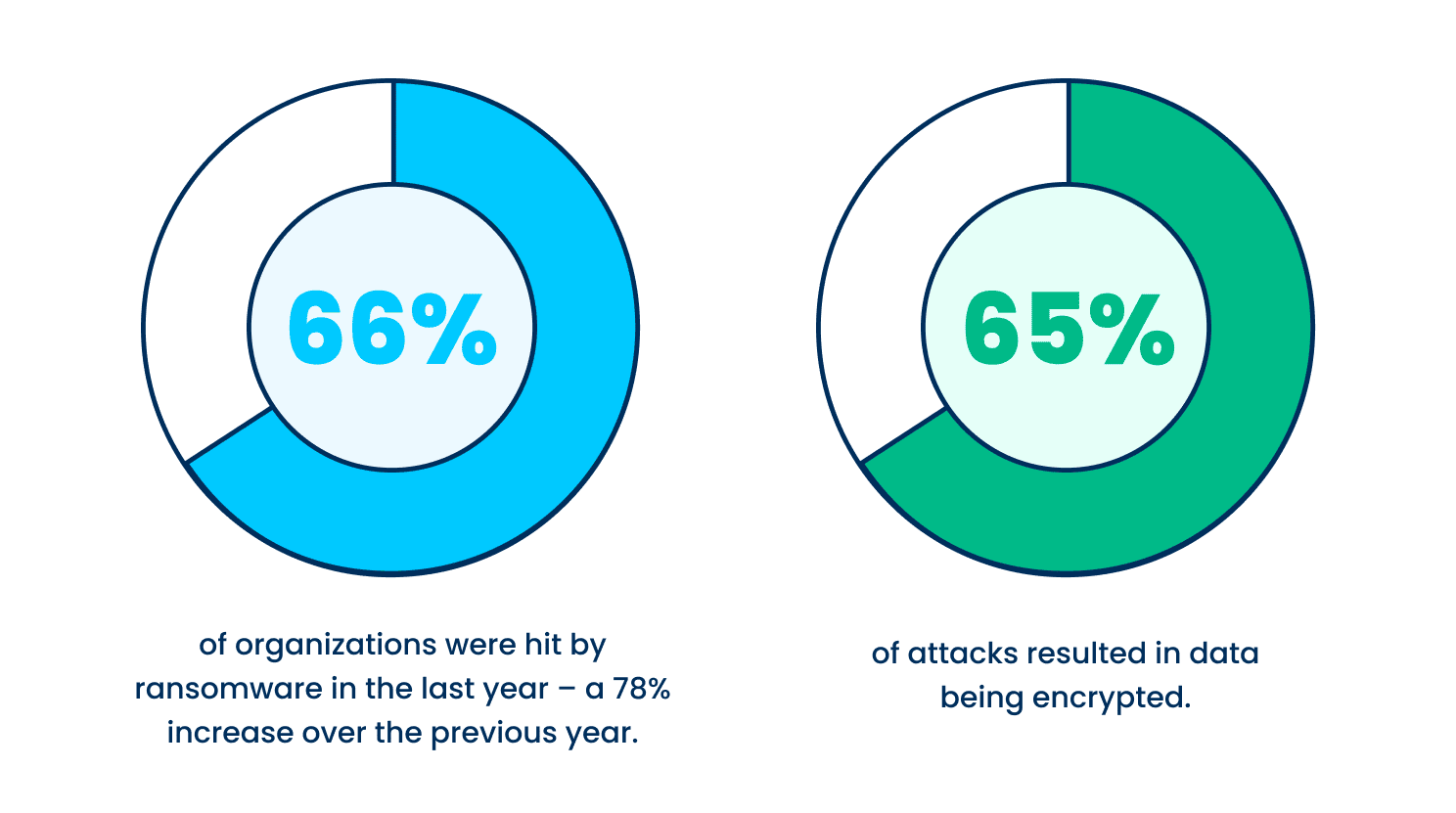
Ransomware attacks have increased significantly over the past year—66% of organizations surveyed were hit by an attack in 2021, up 78% from the previous year. This is due in part to the ease at which bad actors are able to deploy attacks. The Ransomware-as-a-service mode has reduced the skill level needed to attack.
Not only are attacks more prevalent, but the attacks themselves are becoming more successful and more complex. In 2021, 65% of attacks resulted in data being encrypted, up from 54% in 2020. Fifty-nine percent of organizations who experienced cyberattacks saw the complexity of the attacks increase, while 57% saw an increase in the volume of cyberattacks overall.
Data recovery rates are improving
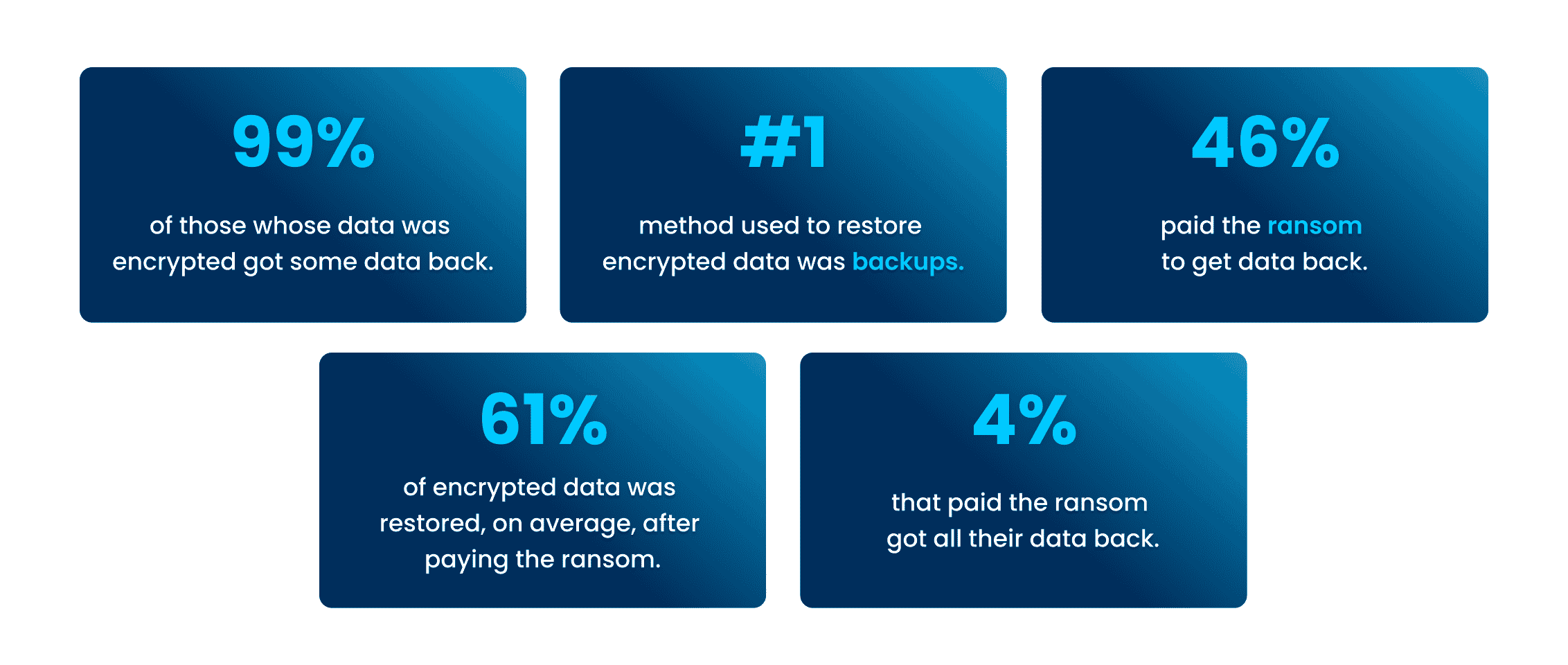
Despite the increase in attacks within the past year, there is some good news. Almost every organization surveyed (99%) were able to get some encrypted data back—up from 96% in 2020. The top method used to restore data was backups, which was used by 73% of organization whose data was encrypted in an attack. In addition to backups, a large portion—forty-six percent—paid a ransom to have their data restored.
Unfortunately, while paying a ransom typically allows organizations to get some data back, it is less effective than in years past at restoring data. On average, organizations that paid a ransom only got back 61% of their data, down from 65% the previous year, while only 4% of those that paid the ransom got ALL their data back in 2021, down from 8% in 2020. This highlights the importance of employing multiple methods to restore data—utilizing backups in particular can improve the speed of recovery and increase the amount of data that can be recovered.
Ransom payments have increased
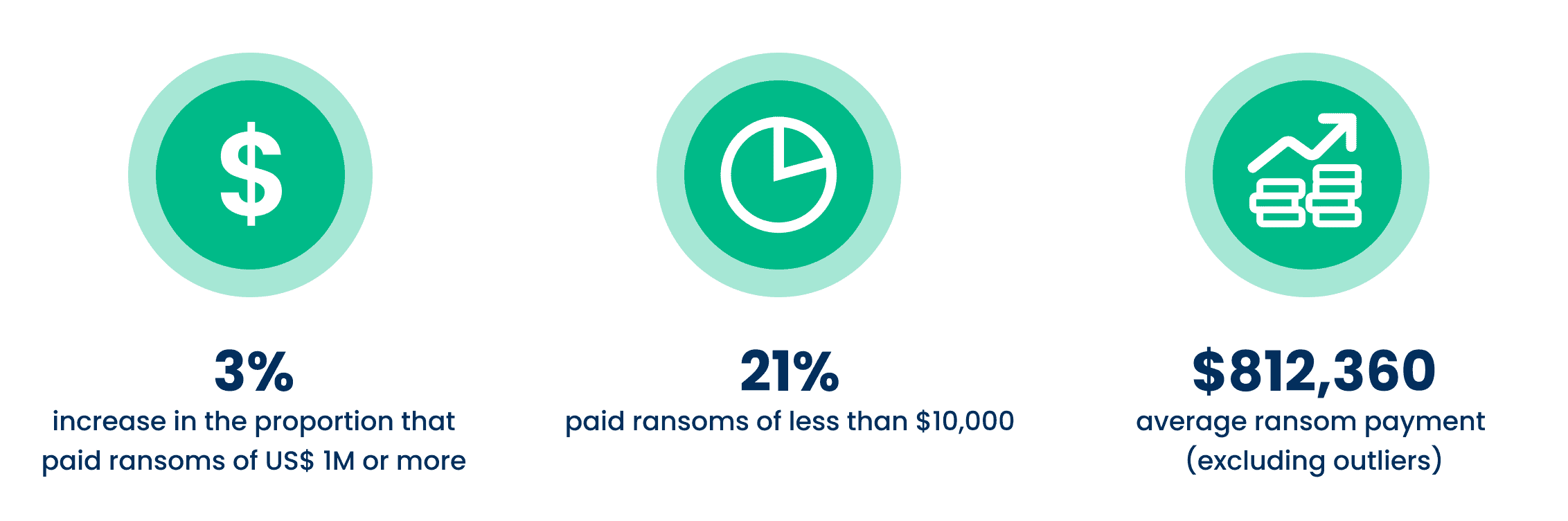
Not only are ransoms less effective at restoring data than in previous years, but the amount of the payments themselves have increased considerably. Between 2020 and 2021 there was a threefold increase in the proportion of victims paying ransoms totaling US$1 million or more. The percentage paying the lowest ransom amounts decreased over that same time—from one in three (34%) to one in five (21%).

The average ransom payout increased 4.8X from 2020 data, from an average of US$170K to US$812,360 in 2021. However, the average ransom amount varies greatly across industries, with manufacturing and utilities coming in at the top of this survey with an average of US$2.04M and US$2.03M, respectively, while healthcare and local/state government had the lowest average ransom payments at US$197K and US$214K, respectively.
Ransomware greatly impacts companies, both economically and operationally
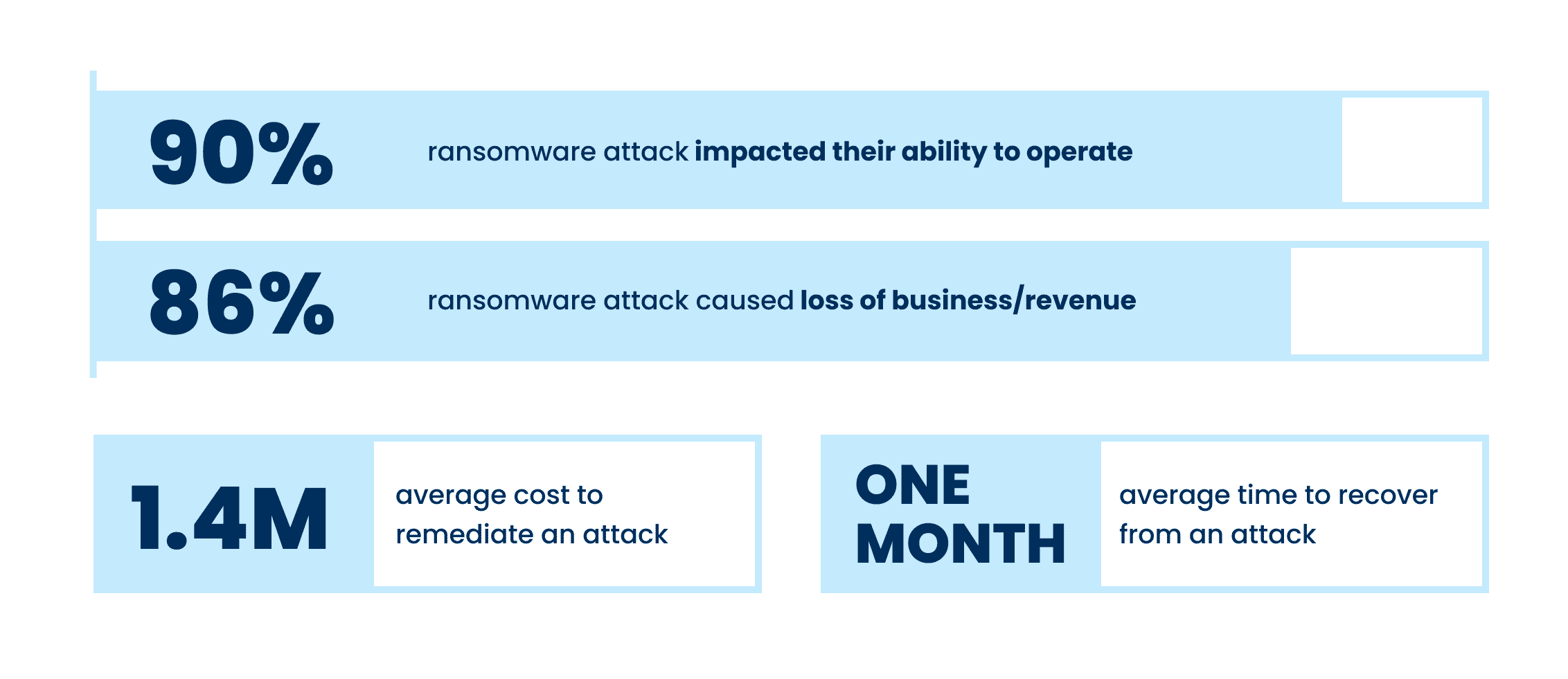
Even when some of all data is able to be restored after a cyber attack, the costs of loss productivity or inability to operate at all can be substantial. Of those hit by ransomware last year, 90% said their most significant attack impacted their ability to operate, while 86% said it caused them to lose business and/or revenue. The average cost to remediate an attack in 2021 was US$1.4M, which, thankfully was down from US$1.85M in 2020. This was due in part to cyber insurance providers being better able to guide victims through an effective response more rapidly.
Although there have been improvements in total recovery time over the years, it still took, on average, one month for organizations to fully recover from the most significant attacks. Those in higher education and central/federal government had the slowest average response times, at around 2-5 months, while manufacturing and financial services were the quickest, with the majority being able to recover in one month or less.
Despite the huge economic costs of ransomware attacks, many organizations are putting their faith in defense that don’t actually prevent ransomware—only more quickly mitigate its effects. Seventy-two percent of organizations in the survey who weren’t hit by ransomware in the past year and didn’t expect to be hit in the future cited backups and cyber insurance as reasons why they don’t anticipate an attack. Neither of these elements actually prevent attacks in the first place.
Simply having security resources in place does not necessary mean that they are effective. Of those surveyed who were hit by ransomware in the last year, 64% said they had more cybersecurity budget than they need, and 24% said they had the right amount of budget. Many of these organization also said they had more headcount or the right amount of headcount (65% and 23%, respectively. This reveals that despite having ample resources—both personnel and technology—organizations will not achieve a high return on investment without a combination of the right technology and expertise to use the technology effectively.
Cyber insurance drives changes to cyber defenses

Thankfully, organizations do not have the shoulder the burden of ransomware costs all on their own. The survey found that four in five mid-sized organizations had insurance against ransomware attacks. However, 34% said there were exclusions/exceptions in their polices. Organizations that had been previous hit by ransomware attacks in the past were much more likely to have cyber insurance coverage against ransomware. However, many respondents indicated that securing coverage has changed in the past year, or gotten more difficult to obtain:
- 54% said the level of cybersecurity they need to qualify is now higher
- 47% said policies are now more complex
- 40% said fewer companies offer cyber insurance
- 37% said the process takes longer
- 34% said it is more expensive
As a result, 97% of organizations that have cyber insurance have made changes to their cyber defense to improve their cyber insurance position. 64% have implemented new technologies/services, 56% have increased staff training/education activities, and 52% have changed processes/behaviors.
Conclusion
The survey has revealed that ransomware continues to be an imminent threat for organizations of all sizes across industries. For many, choosing an experienced partner with expertise in cybersecurity not only improve their chances of getting approved for the right amount of cyber insurance coverage, but can ensure that they see an higher return on investment and improved ability to prevent and mitigate attacks in the future.
The Cost of Skimping on Security in 2022
From 2020 to 2021, the number of ransomware attacks on organizations increased by 78% and more than 10% of those attacks resulted in ransoms of $1 million or higher. According to the Sophos State of Ransomware 2022 report, ransomware attacks take an average of one month to fully recover from and frequently result in downtime and loss of revenue, the impact of which leads to an average recovery cost of $1.4 million. That’s about 640 vacations to Disney World. The cost of skimping on security is great.
While you could take your entire team to Disney World for a week, possibly even a few times over, a better idea might be to invest in preventing a security breach in the first place. Be it ransomware, a phishing attack, or an insider threat, proactive threat and risk prevention takes dedicated time, well-trained people, and cutting-edge technology, so it is no surprise that it can be confusing and costly. As we’ve already seen, it can be even more costly to ignore those risks.
Keeping Up with Technology
It took 2 million years for humans to progress from the first tools to discovering fire, yet it only took 130 years to go from the telegraph to the internet and another 33 years to get to the iPhone. Technology now changes at a blistering pace and, alongside that thrives the unfortunately fruitful business of cybercrime. One of the most critical factors in combating this is having, understanding, and fully utilizing the latest technology. Based on Gartner’s 2022 report of Top Strategic Trends, some of the newest technologies that will impact the cybersecurity field include:
- Cybersecurity Mesh: A scalable, integrated architecture that enables security tools to work cooperatively throughout an environment
- Autonomic Systems: Self-managing systems that take in information from the network to modify algorithms without manual updates, allowing for rapid changes and scalability
Source: Gartner
Partnering with the Experts

Whether you are intimately familiar with the concepts presented here or they sound like something from the USS Enterprise, partnering with experts is what will give you an advantage over bad actors and cyber criminals. Admittedly, most organizations struggle to keep up with regular patching, let alone investing the time and resources into implementing these types of technology. While cybersecurity and understanding cyber risk are likely not your area of expertise, working with a trusted partner can ensure that your online business and IT landscape are as secure as technology and expertise allow. Having security that stands up to the worst of ransomware, hackers, and more is a must.
The criminals don’t take a break, so your security monitoring can’t either, which is why it is critical to have both the technology to meet the needs of today’s risks as well as the people to understand, implement, and manage that technology to its fullest potential. Aunalytics has you covered. With expert toolsets and talent, your business can depend on us to have highly trained professionals and the newest technology and information to protect your business in the ongoing threat landscape.
Bridging the Mid-Market Talent Gap for Digital Transformation
Bridging the Mid-Market Talent Gap for Digital Transformation
To achieve business value from data technology investments, mid-market companies need the right technical expertise and talent. Yet many mid-market firms push this onto their IT manager, assuming that since it is technology related, IT has it. This is a mistake because most IT departments do not have time for data analytics. They are busy full time keeping company systems stable and secure, and providing support to your team members. This by necessity results in IT deprioritizing data queries over crucial cybersecurity attack prevention. Business analysts and executives get frustrated waiting for data query results, and the data is stale or the business opportunity has passed by the time query results are in.

But even if your IT team had time for it, it still is a mistake to rely on traditional technology administrators for data analytics success. This is unless your IT department has expertise across a wide range of skill sets, from cloud architecture, database engineering, master data management, data quality, data profiling, and data cleansing. What’s more, your IT manager would need to have command over data integration, data ingestion, data preparation, data security, regulatory compliance, data science, and building pipelines of data ready for executive reporting from multiple cloud and on premises environments.
When you read this laundry list of needs, it becomes clear that most mid-market IT departments lack the specialized experts needed to derive business value from their data. Unlike larger enterprises that have the resources to hire skilled staff for these roles, the mid midsize organization requires another option that provides access to the right tools, resources, and support. One that integrates, enriches and is trained in utilizing AI, machine learning, and predictive analytics to achieve more useful results.