How To Improve Your Company’s Security Awareness in 2023
We’ve almost made it through 2022, and with every year that passes cyberattacks become more targeted and deceitful. If your organization does not have a Security Awareness Training program in place, you may not know there’s a lot in the digital world that can cause severe distress to you, your coworkers, and your day-to-day operations. Long gone are the days where all we had to be wary of was an email asking you to help a Nigerian prince with their boatloads of money. Technology has come a long way—and so have bad actors trying to get access to your data and disrupt your business operations. Fortunately, there are ways to mitigate these risks.

Social Engineering Attacks
Spam and phishing calls, texts, and emails are everywhere we look—or hear—and these individuals craft their messages in the most believable ways. A relative in the need of some help or your supervisor asking you to buy some gift cards are some of the most common forms the phishing and spam messages might take. The constant barrage of threats requires you to keep a vigilant and informed eye on them. Before a bad actor can get access to the entire company’s vital data, an individual working in that company usually experiences an attack. The victim could be the CTO of a company, a receptionist, or the new intern—anyone is under the risk of a social engineering attack.
Scammers, hackers, and all other types of bad actors in this era of information technology are getting smarter, and we need to pull up our socks and get informed. It’s predicted that, by 2025, there will be an average of 10 devices per person, all connected to the internet and at risk of cyberattack. These devices need to be guarded—not only by cybersecurity services, but also by individual employees.
There are several types of threats out in cyberspace that bad actors deploy to gain access to an organization’s valuable data. The most common and widespread attacks are phishing, spear phishing, vishing, and smishing. Don’t be fooled by the names— these kinds of attacks pose a great deal of trouble unless they can be spotted before they have a chance to coerce or convince someone to unknowingly hurt their organization.
Phishing happens in the form of an email with malicious links or attachments that, if clicked, could give bad actors access to your system or persuade someone to divulge personal information in the form of passwords or credit card numbers. Spear phishing is a highly targeted form of phishing, aiming to attack and exploit one specific person. Spear phishing attacks typically include personal information about you that bad actors can find on social media or other online public forums. Smishing and Vishing are also phishing but in the form of a text message or a phone call.
Employees Can Fight Back By Getting Informed
Employees will need to be able to spot certain indicators that should make them pause before making a decision that might cause a security breach. Often, something will seem out of place with a phishing message, but your employees cannot know what to look for if they aren’t trained to see signs of malicious intent. Vigilance is critical in this scenario because bad actors are making sure that these markers are very difficult to spot. The information below can help employees begin to spot red flags:
- Phishing through emails is the most common form bad actors choose to work with. The following points might not seem like much at first glance, but, if combined, these are a sure sign of a phishing attack:
- Subject lines that have a sense of heightened urgency;
- From unknown and/or unexpected email addresses;
- Different ‘reply-to’ and ‘from’ email addresses;
- Unusual days and times for the email to have been sent—like after work or extremely early on a Saturday;
- Clearly noticeable grammar and spelling mistakes;
- Unnatural wording;
- Unexpected or suspicious links or attachments; or
- An offer for a reward in the form of money or gift cards in exchange for an action that that needs to be taken.
- Text messages also open organizations and people to the same security risks as emails, even though they are a different format. In the case of smishing, most of the red flags for phishing apply, but there are a few more that individuals should take note of:
- The sender claims to be a company executive or direct report with an urgent need;
- The number is different from the number that you might have saved;
- Enquiring about personal information;
- Requesting to follow a link or send money.
- Vishing attacks, or phone call scams are very prevalent and commonly tend to prey on the elderly. These are mainly seen outside the workplace, but they do still pose a threat. The following are some common signs people need to look out for in the case of a vishing attack:
- Unexpected calls from unrecognized numbers;
- Caller requesting access to a digital device to solve an issue;
- Caller threatening legal action and claiming to be from a government body, like the IRS;
- Caller claiming you are a prize winner;
- Caller requesting money in the form of gift cards or asking for personal information like bank details and credit card numbers;
- Caller impersonating an executive, co-worker, or even a family member has found themselves in deep, generic trouble—like getting into a car accident or being arrested—necessitating immediate cash transfers, money wires, and more to get them out of trouble or harm’s way.
Organizations should put a Security Awareness Training program in place to help their employees gain knowledge and experience a behavioral transformation, which would further impact their ability to avoid causing breaches in your organization’s network. Such initiatives ensure everyone in the company is aware of the risks that exist in the digital landscape, and they make decisions that are in the best interests of the organization’s overall security. Each employee is responsible for their organization’s cybersecurity, and if they treat all the information they have access to as a section of the overall information system, the overall system will have significantly higher chances of being secure. If your organization would like to learn more about implementing a Security Awareness Training program, contact Aunalytics today.
The Role of a Data Scientist
The Role of a Data Scientist
In this interview, David Cieslak, PhD, talks about the role of a data scientist—from what a typical workday looks like, to tips for budding data scientists.
David Cieslak, PhD, is the Chief Data Scientist at Aunalytics since its inception and leads its Innovation Lab in the development and delivery of complex algorithms designed to solve business problems in the manufacturing/supply chain, financial, healthcare, and media sectors. Prior to Aunalytics, Cieslak was on staff at the University of Notre Dame as part of the research faculty where he contributed on high value grants with both the federal government and Fortune 500 companies. He has published numerous articles in highly regarded journals, conferences, and workshops on the topics of Machine Learning, Data Mining, Knowledge Discovery, Artificial Intelligence, and Grid Computing.
Banking Institutions Are Behind in AI Maturity—Catch Up or Others Will Eat Your Lunch
Banking Institutions Are Behind in AI Maturity—Catch Up or Others Will Eat Your Lunch
Financial institutions must embrace the use of data analytics powered by artificial intelligence for operational efficiency, risk reduction, revenue growth, and improved customer experience. Yet, it’s clear that financial companies that fail to pick up the pace, moving ahead to the next phase of AI deployment, are in danger of falling far behind. Luckily, there is a clear-cut solution to reaching AI maturity and achieving sustained, long-term success.

Fill out the form below to receive a link to the article.
Banking Institutions Are Behind in AI Maturity—Catch Up or Others Will Eat Your Lunch
Banking Institutions Are Behind in AI Maturity—Catch Up or Others Will Eat Your Lunch
Financial institutions must embrace the use of data analytics powered by artificial intelligence for operational efficiency, risk reduction, revenue growth, and improved customer experience. Yet, it’s clear that financial companies that fail to pick up the pace, moving ahead to the next phase of AI deployment, are in danger of falling far behind. Luckily, there is a clear-cut solution to reaching AI maturity and achieving sustained, long-term success.
The Value of Data Visualization
In this brief video, Dr. David Cieslak, Chief Data Scientist at Aunalytics, discusses the value that data visualization brings to data analytics. Whether you’re using a simple tool such as Excel or a BI software such as Tableau, creating a visual representation of your data allows it to be consumed by a much broader and less technical audience. Whether you’re a marketing specialist, a loan officer, or a bank president, a well-designed and up-to-date dashboard greatly improves your ability to understand and work with your data in a way that lists and spreadsheets can’t.
Aunalytics’ Daybreak Dashboards for Financial Institutions offer a variety of data visualization options such as the Customer Profile dashboard, which provides a 360-degree view of each customer, the Lending KPI dashboard, which provides overall and detailed lending performance across your organization, and the Marketing KPI dashboard, which allows for targeted campaigns to reach the right customer at the right time with the right product. With Aunalytics, you get the technology and the expertise required to turn your disparate data into easily understandable insights through the Daybreak Dashboards.
David Cieslak, PhD, is the Chief Data Scientist at Aunalytics since its inception and leads its Innovation Lab in the development and delivery of complex algorithms designed to solve business problems in the manufacturing/supply chain, financial, healthcare, and media sectors. Prior to Aunalytics, Cieslak was on staff at the University of Notre Dame as part of the research faculty where he contributed on high value grants with both the federal government and Fortune 500 companies. He has published numerous articles in highly regarded journals, conferences, and workshops on the topics of Machine Learning, Data Mining, Knowledge Discovery, Artificial Intelligence, and Grid Computing.
How An End-to-End Analytics Solution Helps You Avoid Hidden Costs
As the new year approaches, digital transformation should be at the top of every mid-market organization’s to-do list. As organizations begin to understand the value of business analytics for their daily operations, the need for an end-to-end analytics solution becomes evident. Yet, many companies struggle to obtain the right analytics solutions to fit their specific needs.
Unfortunately, the analytics solution market can be difficult to navigate. Since building an analytics tool in-house is incredibly time-consuming and very costly, many mid-market companies would be better served by working with a solution provider who can provide both the tools and talent necessary to achieve their business goals.
Digital Transformation Roadblocks
One major roadblock in the pursuit of digital evolution is determining how much an analytics solution is going to cost. Analytics solutions are complex, and when an analytics company gives a quote, they often fail to mention additional add-ons their solution needs to be functional. For instance, charges for a third-party cloud to host your analytics solution and individual charges for connectors that allow your disparate data sources to flow into the solution are the most common up-charges.
Your organization could get stuck with unexpected licensing fees or overage charges from a third-party cloud provider. Worse yet, you may end up piecing together various technologies, while lacking the adequate technical talent to keep the solution functioning and show actionable results. To achieve value from your investment, it is vital to look for a partner that can provide you with a solution where extra charges do not come into play. Budgets are an integral part of the decision-making process when it comes time to choose a solution provider.
With hidden costs, figuring out how a particular solution is going to fit into your budget becomes increasingly difficult. The most effective solution is opting for a partner who can provide your company with an end-to-end analytics solution.
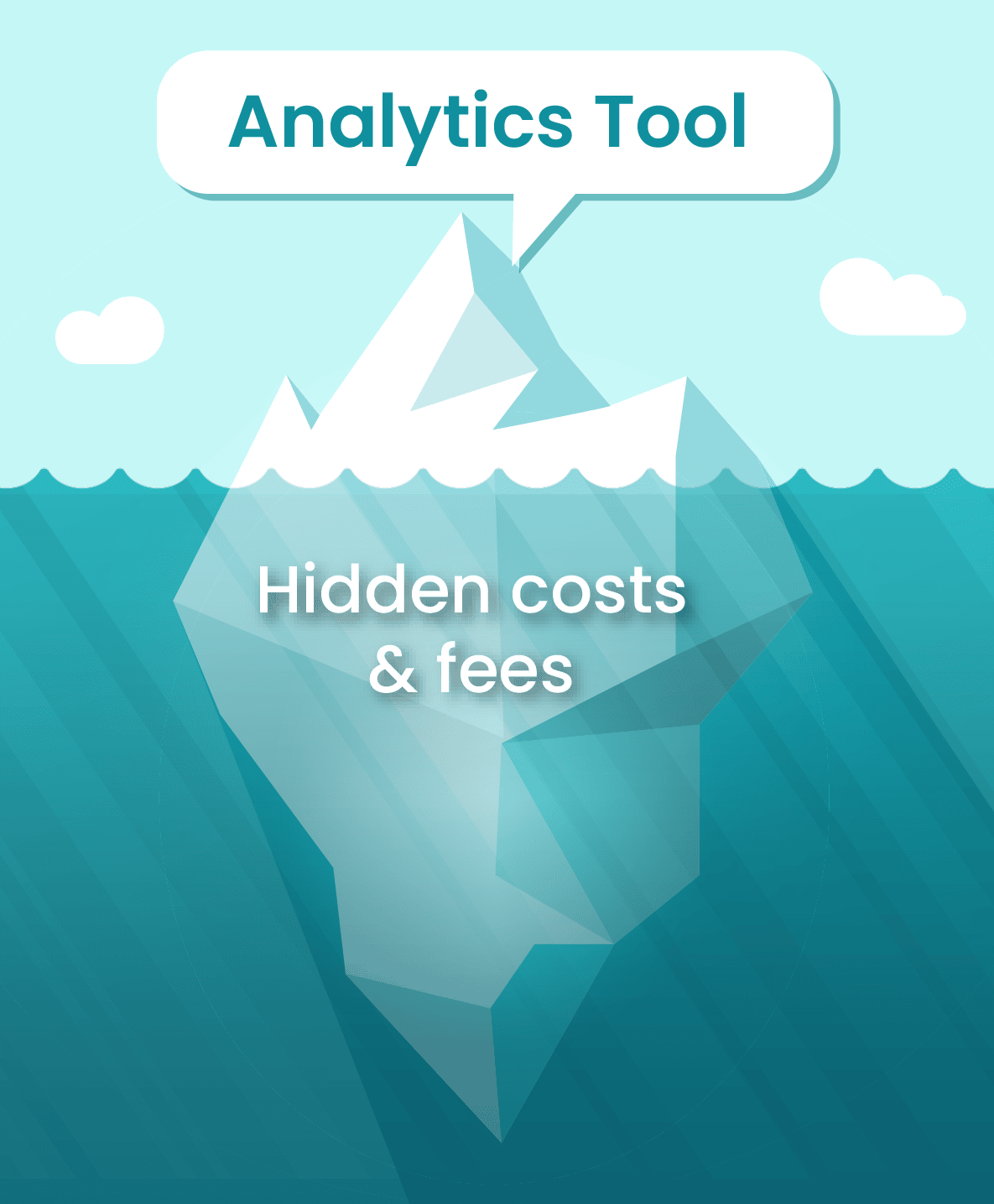
Why Mid-Market Organizations Need End-to-End Analytics Solutions
To compete with larger institutions, mid-market organizations need to leverage their existing local data to gain insights to better serve their clients. An end-to-end solution ensures you do not end up with a solution your team cannot utilize to achieve your business goals and thrive in an increasingly competitive market.
It is a known fact that mid-market businesses struggle with retaining talent for data management, IT, security, and advanced analytics. Opting for an end-to-end solution gives you access to a team of experts who will always be by your side, assisting you every step of the way.
With Aunalytics, you get the technology and the expertise required to complete your journey from disparate data to actionable business results. Using our platform, your entire organization can reap the benefits of having a reliable and robust data platform.
Aunalytics Provides a Complete, End-to-End Analytics Solution for Mid-Sized Organizations
Aunalytics offers an end-to-end analytics solution that includes the right technology paired with experts who work by your side to help you accomplish your business goals. The technology, combined with the technical talent necessary to fully utilize it, will help your organization achieve true value from your investment. End-to-end analytics solutions provide you with insights from your data so you can concentrate on critical business decisions. No longer do you have to worry about overages, licensing costs or other additional charges. Aunalytics has the answers to your business and IT questions.
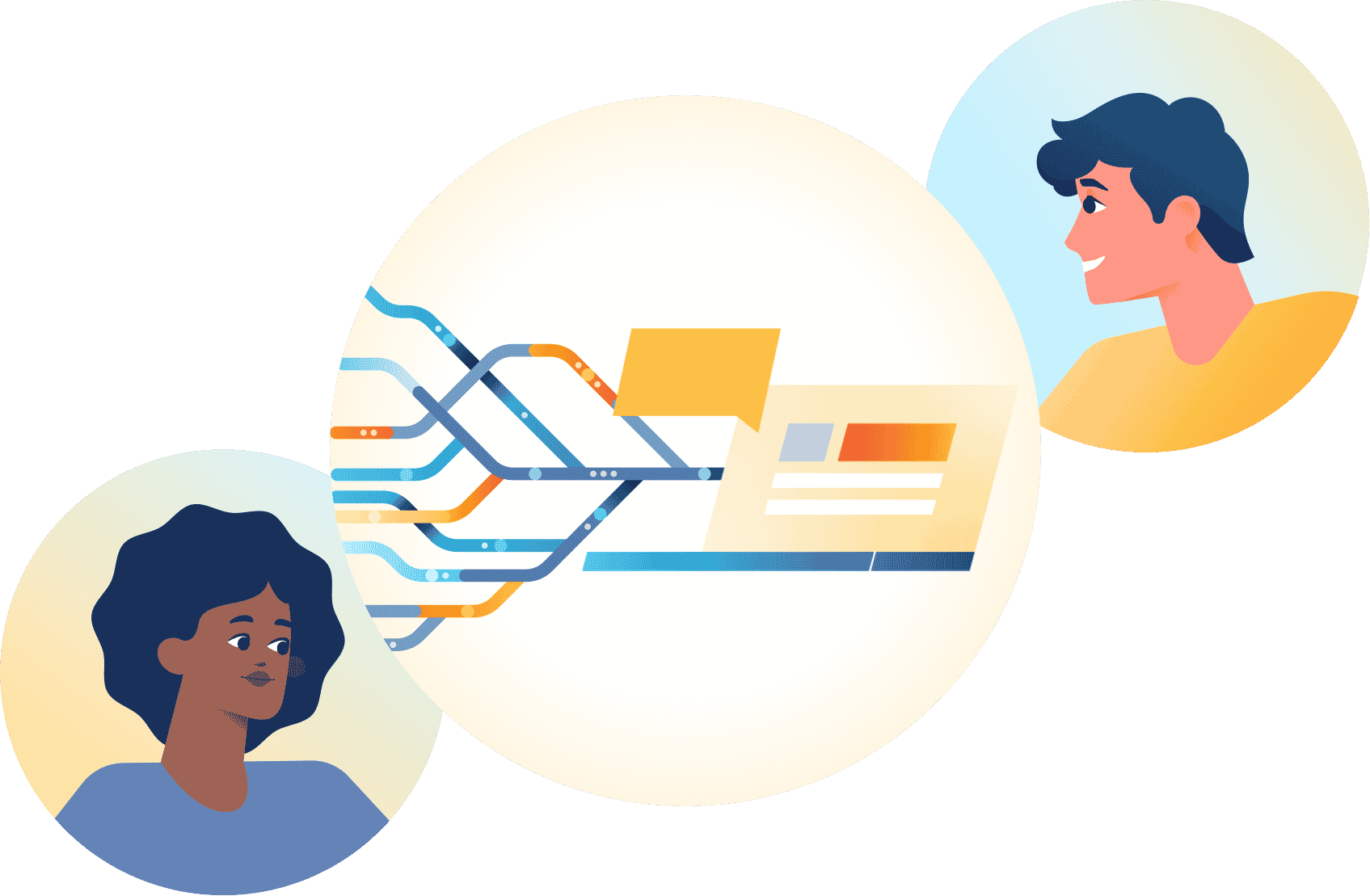
The Aunalytics Data Platform is a robust, cloud-native data platform built for universal data access, powerful analytics, and AI. It includes the following components:
- Aunalytics Enterprise Cloud provides a highly redundant, secure, and scalable platform for hosting servers, data, analytics, and applications at any performance level.
- Aunsight Golden Record integrates and cleanses siloed data from disparate systems for a single source of accurate business information across your enterprise.
- Daybreak Analytics Database provides daily insights powered by Artificial Intelligence (AI) and Machine Learning (ML) driven analytics, industry intelligence, and smart features that enable a variety of analytics solutions and timely actionable insights that drive strategic value across your company.
This end-to-end platform enables your business to extract answers from your data without having to worry about additional charges that might break your budget. Our solutions are secure, reliable, and scalable, all according to your business’ needs. Aunalytics solutions seamlessly integrate and cleanse your valuable data for accuracy, ensuring data governance and employing Artificial Intelligence (AI) and Machine Learning (ML) driven analytics to glean customer intelligence and timely actionable insights that drive strategic value.
Using our solution, team members across your organization can reap the benefits of having an end-to-end analytics solution to make data-driven decisions. Company executives can view data cleansed into an accurate golden record that is streamed in real-time to enable better decision making for the entire organization. Your organization’s marketing team can have access to aggregated data that reveals a 360-degree view of your customer, including insights into customer behavior, that empowers them to run data-driven campaigns to the right customer, at the right time, with the right product. Your IT department can ensure that you are functioning at peak efficiency by analyzing the data collected to scale resources and identify potential roadblocks and bottlenecks. Those are just a few departments that would benefit—think about how powerful a real-time analytics solution could be across your entire organization.