Carolinas' LAUNCH 2025
Carolinas' LAUNCH 2025
Embassy Suites by Hilton Charlotte Concord, Concord, NC
Aunalytics to attend Carolinas Credit Union LAUNCH 2025
Aunalytics is thrilled to be an exhibitor at the Carolinas Credit Union LAUNCH 2025 in Concord, NC on February 12-13, 2025. Aunalytics will be at booth #1 to educate credit union stakeholders on how our technology solutions can make their jobs easier and more effective.
The Sightglass Productivity Platform enables credit unions to use AI to increase deposits and more effectively identify and deliver new services and solutions—allowing them to compete with large national banks. Aunalytics also partners with credit unions to deliver cloud, backup, and managed IT solutions that are robust and secure—streamlining the implementation process and providing solutions as-a-service.

Understanding the Hackers' Playbook: How to Prevent Cyberattacks and Adopt Good Practices
As increasingly sophisticated cyber threats pose risks to companies of all sizes, understanding how to prevent cyberattacks and implement good safety practices is important for any organization. This blog post discusses the common threats that companies face, effective cybersecurity strategies, and best practices for maintaining robust defenses. We’ll also explore how to foster a culture of security awareness and prepare for rapid recovery after an incident.

Understanding Common Cyberattacks
To effectively combat cyberthreats and develop smart strategies, organizations must be able to recognize common threats. One increasingly common type of attack is an opportunistic attack—attacks based on available opportunities rather than specific targets. One of the most prevalent opportunistic attacks involves exploiting known vulnerabilities—weaknesses in software or systems that, if left unpatched, can be leveraged by hackers to gain unauthorized access. For example, the Experian data breach demonstrated the dangers of neglecting known vulnerabilities. Despite being aware of the issue for weeks, Experian’s IT team failed to act, resulting in a massive compromise of personal data. This incident highlights the importance of timely patch management and proactive security measures.
Another critical threat is the compromise of business email accounts, often leading to the exploitation of platforms like Office 365. Common risk factors include the lack of Multi-Factor Authentication (MFA) and poor security practices. While MFA can significantly reduce the risk of unauthorized access, many organizations still avoid implementing it, often due to perceived inconvenience. However, the benefits of MFA far outweigh the hassle, making it a fundamental component of a strong security posture.
While technologies such as MFA are extremely effective at preventing cyberattacks, it doesn’t prevent all breaches. Phishing, though a simple, well-known concept, remains one of the most effective and damaging methods of cyberattack. Phishing emails trick recipients into divulging sensitive information or clicking on malicious links. It is all too easy for a single employee to have a brief lapse in judgement that puts an organization at risk. To combat this, phishing-resistant MFA and ongoing employee training are essential.
Key Components of an Effective Cybersecurity Strategy
To build a robust cybersecurity strategy, it’s essential to implement layered defenses and understand the key principles of security management. Phishing-resistant MFA adds an extra layer of security by requiring multiple forms of verification before granting access. This makes it significantly harder for attackers to gain unauthorized access through stolen credentials.
Additionally, understanding the shared responsibility model is crucial. Organizations must know their responsibilities and choose technology providers that align with their security needs. This includes ensuring that all security measures are covered and that responsibilities are clearly defined.
Employing established security frameworks, such as the NIST Cybersecurity Framework (CSF), can also provide a structured approach to managing and mitigating cybersecurity risks. These frameworks offer guidelines on identifying, protecting, detecting, responding to, and recovering from cybersecurity incidents.
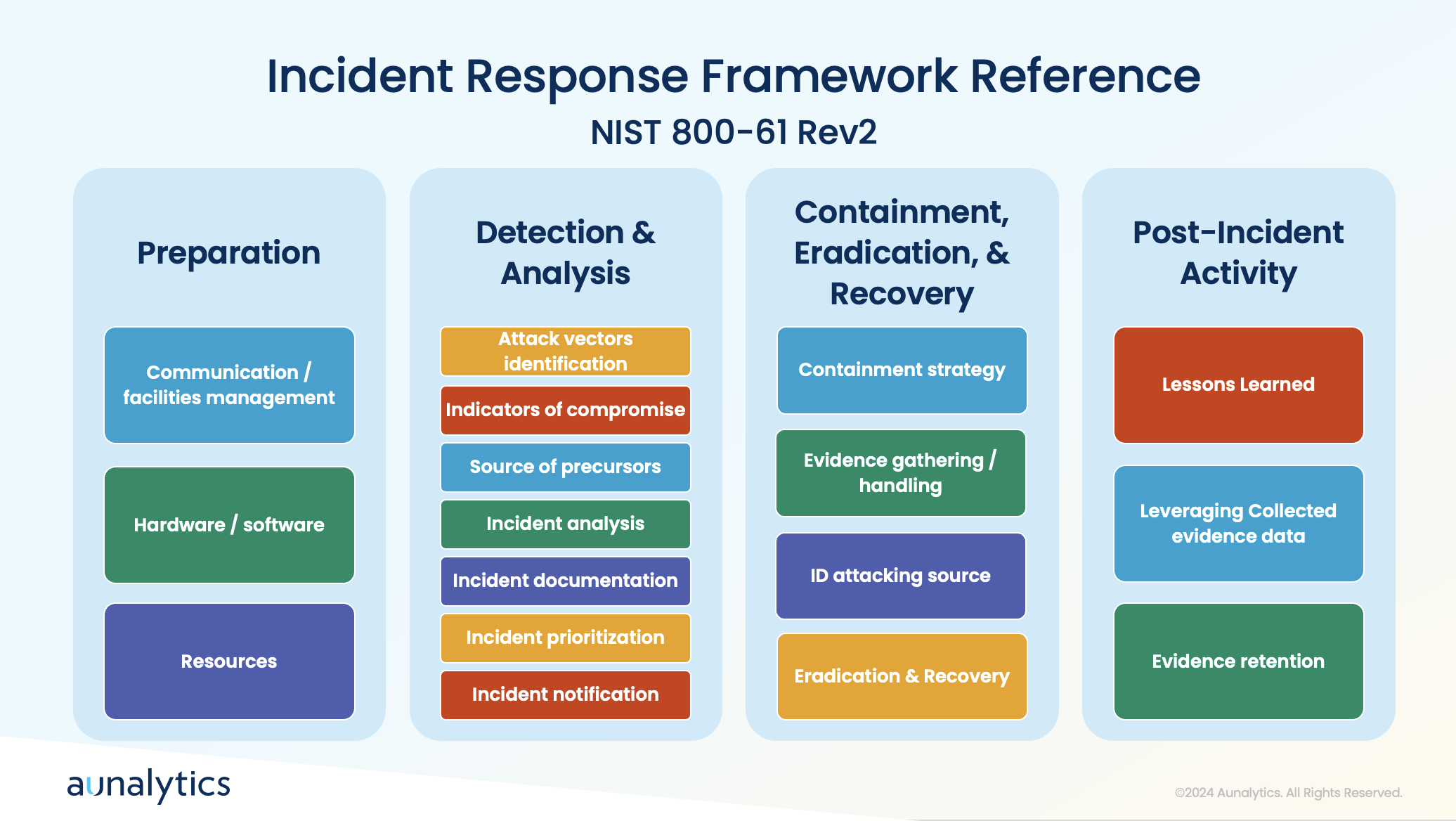
Keeping Cybersecurity Policies Up-to-Date
Security threats are constantly evolving as hackers develop increasingly complex methods and uncover new vulnerabilities. To maintain a strong cybersecurity posture, organizations must continuously adapt their strategies—regularly reviewing and updating policies is essential. This includes conducting periodic assessments and audits to ensure that policies remain effective and relevant. It is also beneficial to regularly test and refine response plans by conducting tabletop exercises to simulate cybersecurity incidents. These exercises help organizations prepare for real-world scenarios and improve their incident response strategies.
As tactics evolve and new vulnerabilities are uncovered, organizations must stay informed of the latest security news and intelligence. This can include gathering threat intelligence from partners and industry sources, and staying informed through news articles, social media, and threat intelligence feeds. Additionally, engaging in a crowdsourced approach to security allows organizations to tap into a broader pool of knowledge and expertise. Participating in cybersecurity forums and collaborating with external security experts can take this knowledge a step further and helps organizations learn how to proactively address potential risks.
Best Practices for Incident Response
While putting safeguards in place to prevent cyberattacks from occurring is imperative, it is also equally important to prepare your organization to respond appropriately when an incident does occur. During a cyberattack, it’s crucial to have tools in place to detect anomalies and communicate effectively. Quick actions include containing the incident by taking affected systems offline, blocking access to malicious platforms, and assessing the scope of the breach.
A clear communication plan and understanding of the attack’s attribution are essential for effective recovery. Preparation involves establishing processes for detection, analysis, containment, eradication, and recovery, followed by post-incident activities to improve future responses.
Employee Training and Awareness

To ensure that all areas of a company take an active role to prevent cyberattacks, it’s crucial to foster a strong security culture. Unfortunately, employees often make mistakes that lead to breaches, such as falling for phishing schemes or responding to solicitation calls. Educating staff about the tactics used by attackers, such as impersonation and social engineering, can help prevent these errors.
Therefore, it is crucial to ensure that all employees have access to cybersecurity training—this training covers the basics of recognizing bad actors and avoiding common traps.
Tailoring training to specific roles and conducting phishing email simulations can enhance employees’ ability to identify and respond to threats. Creating a culture of cybersecurity awareness involves emphasizing the importance of security to employees and their families. This helps instill a sense of personal responsibility for maintaining security practices.
For IT and cybersecurity professionals, it is greatly beneficial to focus on developing a strong understanding of network engineering, including routing, switching, and firewall management. Additionally, the ability to visualize and comprehend data flows and security information is crucial for effective security management. IT teams must avoid cutting corners and ensure robust security measures are in place. They play a critical role in enforcing security policies and preventing breaches, making their diligence essential.
Conclusion
Understanding the tactics used by attackers and implementing robust preventive measures is key to safeguarding your organization. By adopting best practices such as phishing-resistant MFA, regularly updating policies, leveraging threat intelligence, and training employees effectively, companies can significantly reduce their risk of cyberattacks. Additionally, having a well-defined incident response plan and fostering a culture of security awareness ensures preparedness for any potential breaches. By following these guidelines, organizations can better protect their data and maintain a strong defense against cyber threats.

Partnering with Aunalytics ensures your data privacy and security through a comprehensive approach that includes advanced risk assessments, phishing-resistant Multi-Factor Authentication (MFA), and continuous updates to align with industry standards like the NIST Cybersecurity Framework. Our expert team provides 24/7 monitoring and rapid threat response, leveraging cutting-edge technology and threat intelligence to preemptively address risks. With Aunalytics, you benefit from top-tier protective measures and a commitment to adapting strategies to emerging threats, ensuring your data remains secure and confidential.
Staying Secure: Recent Security Breaches and Essential Prevention Strategies
The increasing reliance on digital technologies has led to the increased frequency of security breaches. Recent incidents have highlighted vulnerabilities across several industries, emphasizing the importance of robust cybersecurity measures. Here, we examine some notable security breaches that have recently made headlines, detailing the “how” and the responses taken to mitigate future risks.

Microsoft Azure and Executive Accounts
In a significant cyberattack on Microsoft Azure in January 2024, hackers exposed the accounts of hundreds of Microsoft senior executives to unauthorized access, with the use of phishing attacks and malicious links. The attackers used a password spray attack to break into the accounts, which is when an attacker tries several passwords across multiple user accounts to avoid detection systems. This breach allowed unauthorized access to Microsoft email accounts, leading to the exfiltration of sensitive emails and attached documents. The attackers also targeted source code and infrastructure, emphasizing the importance of heightened vigilance against sophisticated phishing tactics.
One extremely effective way to ward against this type of attack is to create strong passwords and change them regularly to prevent them from being hacked, as well as using multi-factor authentication.
Bank of America Third-Party Data Breach
Attackers understand that large banks have robust cybersecurity measures to protect their networks. However, many third parties lack similar resources and may not yet prioritize cybersecurity education or infrastructure. This makes them more likely to be targets for cybercriminals seeking vulnerabilities to exploit when sharing data with major institutions. This incident underscores the critical need for financial institutions to strengthen third-party vendor security protocols and ensure robust data protection measures.
The ransomware group LockBit orchestrated a breach targeting Bank of America in February 2024 via its third-party vendor, Infosys McCamish. Personal information—including names, Social Security numbers, and account details of over 57,000 individuals—was compromised.
Ascension Ransomware Attack
Such attacks necessitate comprehensive cybersecurity strategies to safeguard critical healthcare infrastructure and ensure uninterrupted patient care. Moreover, ensuring robust disaster recovery plans and reliable backups can get services back on track faster, which is particularly crucial for healthcare systems, because extended delay can directly impact patient care and safety.
Ascension, the owner of 15 hospitals in Michigan, fell victim to a ransomware attack in May 2024 that disrupted electronic health records systems, phone systems, and scheduling processes. Non-emergency procedures and appointments were suspended, highlighting the operational impact of cybersecurity incidents on healthcare services.
New York City Metropolitan Transportation Authority (MTA) Cyberattack
In 2020, research showed that municipalities, which are already vulnerable targets for cybercrime, faced 44% of global ransomware attacks—equating to approximately 133,496,000 incidents. An April 2021 cyberattack on the New York City Metropolitan Transportation Authority (MTA) compromised 18 systems, including those controlling train operations and safety mechanisms. This breach posed serious implications for public safety and operational continuity.
Following the attack, MTA swiftly implemented federally recommended security enhancements and mandated password changes and VPN switches for employees and contractors, illustrating proactive steps to fortify cybersecurity defenses.
Moving Forward: Prevention Procedures
Preventing security breaches requires a multi-faceted approach that empowers teams and safeguards organizational assets. Regular training sessions are essential to educate employees on identifying phishing emails, creating robust passwords, and understanding the importance of safeguarding sensitive information. This measure ensures everyone understands their role in preventing data breaches.
Strengthening asset management through classification, organization, automation, and continuous monitoring helps maintain an up-to-date inventory, facilitating informed decision-making and enhancing troubleshooting capabilities. Effective management and monitoring of access rights, supported by IAM, routine account audits, SSO, and multi-factor authentication, are also critical for ensuring only authorized personnel have access to certain resources.

Another strategy to prevent security breaches is implementing robust firewalls and antivirus software services, which can serve as the frontline defense against malicious threats. Regular updates to these defenses are crucial to identifying and addressing vulnerabilities promptly. Additionally, implementing automated data backup systems across multiple locations provides a safety net against data loss and physical damage, ensuring business continuity even in the face of unforeseen incidents. By integrating these preventive measures into comprehensive cybersecurity strategies, organizations can effectively mitigate risks and protect sensitive information from increasingly sophisticated cyber threats.
At Aunalytics, we are committed to preventing security breaches—protecting customer data is our top priority. We adhere to stringent security protocols, including regular employee training, robust encryption measures, and continuous monitoring of access controls. Our goal is to ensure our clients are utilizing the latest security technologies and best practices to stay protected, while having the right backup and disaster recovery strategies in place to get their businesses back up and running as quickly as possible in the event of a cyber event or disaster scenario.
Immutable Backup: Its Crucial Role in Safeguarding Your Data
In today’s digital landscape, where cyberthreats pose a significant threat and unforeseen disasters can strike at any moment, ensuring the security and integrity of your data is crucial. But what exactly is an immutable backup, and why is it so important?
What is immutable backup?
Immutable backup, simply put, means data that is incapable of being changed or altered. It serves as a safeguard against various threats, including ransomware attacks, malware, viruses, equipment malfunctions, human errors, and natural disasters. An immutable backup is a way of protecting data that ensures the data is fixed, unchangeable, encrypted, or unable to be modified.
The significance of immutability cannot be overstated, especially when considering the prevalence of ransomware attacks. Such attacks can take months for businesses to recover from. In a ransomware attack, an organization’s data or systems are encrypted by an attacker and a ransom is demanded before the organization can regain control of its data. What’s worse, traditional backup and recovery systems are often targeted by cybercriminals, leaving organizations vulnerable even in their supposed safety nets.
Immutable backups offer a critical defense against ransomware, ensuring that your data remains resistant to both internal and external threats. It can be accessed any number of times but cannot under any circumstances be written over. In the event of data loss, immutable backups enable swift and seamless restoration, minimizing downtime and facilitating the quick resumption of business operations. The benefits of implementing immutable backups include enhanced data protection, rapid recovery in the event of data loss, peace of mind, meeting compliance and legal requirements, and digital evidence preservation.
How does immutable backup work?
So, how do immutable backups function? When establishing an immutable backup, a pivotal step involves instituting an “object lock” on the data. This lock ensures the data remains unaltered for a specified duration, determined by the user initiating the backup. Throughout this timeframe, the data remains inaccessible but is shielded from any attempts at manipulation or deletion. Upon the lock’s scheduled expiration, the backup is no longer immutable. While it’s possible to make a backup immutable indefinitely, it’s not typical because every organization’s data changes over time. Therefore, periodic replacement of the backup with a new immutable record is necessary to ensure it remains up to date and adequately protected.

Aunalytics Immutable Backup Solution
At Aunalytics, our immutable cloud backup solution ensures that backup storage repositories in the Aunalytics Cloud cannot be deleted or modified, providing robust protection for your data. A secondary repository that allows for object locking is created within the Aunalytics Cloud tenant portal to the specifications of the customer. The customer creates backup jobs for this repository, and schedules them as they see fit. As the need for storage increases (or decreases), the environment will grow with it.
If the customer is also utilizing Aunalytics Managed Services for their servers, the Managed Service Team (Centralized Services) will manage these backups for the customer. At Aunalytics, safeguarding customer data is of the utmost importance. We uphold stringent measures to ensure the confidentiality, integrity, and availability of all data entrusted to us. Our commitment to data protection is not just a policy—it’s a culture woven into every aspect of our operations, fostering trust and reliability among our valued customers.
2024 Ohio Information Security Conference
2024 Ohio Information Security Conference
Sinclair Conference Center, Dayton, OH
Aunalytics to Attend and Speak at the 2024 Ohio Information Security Conference
Aunalytics is excited to attend the 2024 Ohio Information Security Conference presented by Technology First in Dayton, OH as a Gold Sponsor. The Aunalytics team is excited to connect with fellow IT professionals to discuss security and innovation in the technology field. Kerry Vickers, CISO of Aunalytics will be joining Max Aulakh, President and Founder of Ignyte, to present “Incident Response Live!” —a tabletop group exercise from 1:30-2:30pm.

2023 Technology First Taste of IT Conference
2023 Technology First Taste of IT Conference
Sinclair Conference Center, Dayton, OH
Aunalytics Is Excited to Attend the 2023 Technology First Taste of IT Conference
Aunalytics is excited to attend the 2023 Technology First Taste of IT Conference in Dayton, OH as a Gold Sponsor. The Aunalytics team is excited to connect with fellow IT professionals to discuss security and innovation in the technology field.

Organizations Shift to Cloud-Based Analytics and IT Platforms
The growth rates of cloud-based IT solutions in the areas of analytics and artificial intelligence have been substantial in recent years. The increasing volume of data and the need for faster, more accurate insights have driven organizations to adopt cloud-based analytics solutions at a rapid pace. This has resulted in the growth of cloud-based data warehousing, business intelligence, and big data analytics solutions.
Similarly, the growth of artificial intelligence has been driven by the cloud, as it allows organizations to access powerful AI algorithms and training data without having to invest in expensive hardware. The cloud has also made it possible for organizations to scale AI solutions quickly and easily, leading to an increase in the adoption of cloud-based machine learning and deep learning solutions. These trends are expected to continue as organizations look to leverage the power of AI and analytics to gain a competitive edge in the market.
This growth in cloud-based analytics and AI has been driven by the larger business adoption of cloud IT because of its numerous benefits such as increased flexibility, scalability, and cost savings. Cloud technology allows companies to access their data and applications from anywhere, reducing the need for physical infrastructure and freeing up resources for other areas of the business. This shift towards cloud computing has also improved disaster recovery and business continuity, as data can be stored and accessed remotely. Additionally, with the rise of cloud-based solutions, businesses have been able to access advanced technologies and services without having to invest in expensive hardware and software. This has resulted in increased competitiveness, innovation and better overall business performance.
APIs add efficiency and flexibility to cloud environments
The power behind the most widely adopted cloud platforms are APIs (Application Programming Interfaces), which play a crucial role as they allow different software systems to communicate with each other and access data from the cloud. This has enabled organizations to build custom solutions and integrate disparate systems seamlessly, making the use of cloud technology much more efficient and flexible.
APIs also allow for automation and streamlining of processes, reducing manual errors and freeing up time for more valuable tasks. APIs make it possible to add new functionality and services to existing systems, allowing for continuous improvement and innovation. In essence, APIs provide a bridge between the cloud and an organization’s systems, enabling organizations to harness the full potential of cloud computing and drive digital transformation.
Analytics moves to the cloud
In terms of business outcomes, cloud-based analytics allow businesses to access and process large amounts of data in real-time, regardless of the size or location of their operations. This enables organizations to make informed decisions quickly and respond to changing market conditions with agility. Secondly, these solutions are much more cost-effective, as businesses only pay for what they use and do not have to invest in expensive hardware or IT infrastructure. The cloud provides businesses with access to a wide range of advanced analytics tools and technologies, enabling them to gain insights from their data in new and innovative ways. These solutions are highly secure and reliable when they are managed by experienced cloud service providers who ensure that data is protected and the solution is always available. Overall, they are considered to be a better choice for businesses because of their scalability, flexibility, cost-effectiveness, and secure approach to data analysis.
Likewise, cloud-based AI or AI as a Service (AIaaS) provides organizations with access to deep insights without having to invest in expensive experts or the necessary hardware and software to implement such solutions. This makes it easier for organizations to deploy and scale AI solutions as they only pay for what they use and do not have to invest in maintaining their own infrastructure. Furthermore, these solutions are more flexible and can be customized to meet specific business requirements, enabling organizations to generate valuable insights that help them to differentiate from their competitors. Finally, cloud-based AI makes it possible for organizations to collaborate and share AI models, allowing them to leverage the collective expertise of their partners, customers, and employees to create better solutions. In short, it is a high-value choice for businesses as it provides a more accessible, scalable, affordable, and collaborative approach to artificial intelligence.
Moving to the cloud accelerates digital transformation
Leading research and advisory firm Gartner reported that “Cloud migration is not stopping, IaaS will naturally continue to grow as businesses accelerate IT modernization initiatives to minimize risk and optimize costs. Moving operations to the cloud also reduces capital expenditures by extending cash outlays over a subscription term, a key benefit in an environment where cash may be critical to maintain operations.”
Aunalytics provides a highly redundant and scalable cloud infrastructure that enables midsized businesses to reap the benefits of the cloud at a reasonable cost. The Aunalytics Cloud provides a wide range of solutions—including cloud storage, backup and disaster recovery, application hosting, advanced analytics, and AI. Moving from on-premises computing to a cloud environment is a key step in an organization’s digital transformation.
VMUG Indianapolis UserCon 2023
VMUG Indianapolis UserCon 2023
The Westin Indianapolis, Indianapolis, IN
Aunalytics to Attend VMUG User Group Indianapolis as a Bronze Sponsor
Aunalytics is excited to attend the VMWare User Group’s 2023 UserCon – Indianapolis. Aunalytics is participating as a Bronze sponsor and our team is excited to connect with fellow IT professionals to discuss digital transformation and innovation in the technology field.

Financial Institution Cyber Attacks Are on the Rise—Your Institution Is Not Immune
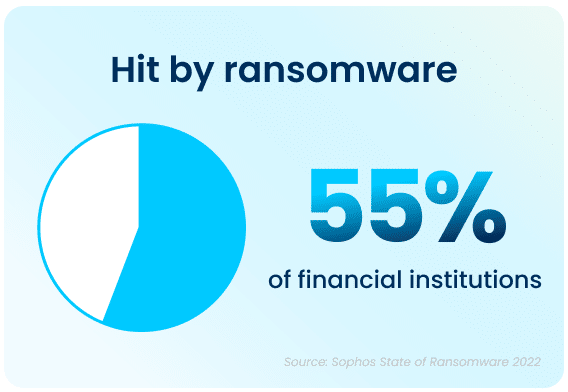
With recent uncertainty in the economy and bank closures hitting the news this year, you may be scrambling to find ways to increase deposits to protect your institution. But a larger, more urgent risk has always been lurking. With over half of financial institutions reporting cyber attacks in a single year, your organization may be next.
Nearly every day we learn of new horror stories from financial institutions who were the victims of elaborate attacks—in fact, 55% reported being a victim of a cyber-attack in a single year.
Bad actors are becoming more sophisticated in their methods. These prevalent attacks have high costs to your business uptime and productivity. A bad attack can also damage your reputation due to closure and data loss, while still costing your bank or credit union large sums of money to pay off ransoms—and you may not even get all of your data back.
Financial institutions hit by cyber-attacks pay, on average, $272,655 in ransom payments. And the average overall cost to remediate the ransomware attack in this sector is $1.59 million.
Do you know where your data lives?
Where you store your data matters, and your storage location may not be optimal for disaster recovery. Storing your backups locally, even if located at another of your facilities, may not protect your data from unknown risks.
In-house servers require large capital expenditures, and you miss out on economies of scale for regular upkeep and maintenance. Giant vendors may seem convenient, but you won’t know exactly where your data resides, and you lose control over the environment.
There’s a better way—Aunalytics backup and disaster recovery solutions can help you avoid losing data or paying large ransoms. We offer concierge solutions tailored to community banks and credit unions—helping you stay steps ahead of increasingly malicious attackers.
Backup and disaster recovery solutions enable the continuous operations of an organization during a disaster event, whether it involves a set of networks or servers, or when all primary IT services have become unavailable. Our solutions leverage the power of data, analytics, and Machine Learning. Disaster Recovery Services, coupled with a comprehensive backup and archival strategy, allow you to remain confident that you are prepared should your business encounter a disaster event.




