Local and State Government Cyberattacks Prove that Security is a Necessity
Cyberattacks are a constant threat to organizations of all sizes. State and local governments are no different, having experienced significantly more cyberattacks than they did in previous years, and are at very high risk of bad actors slipping into their networks. To gain a better understanding of the current attack environment and track changes over time in ransomware trends, Aunalytics security partner Sophos commissioned an independent, vendor-agnostic survey of 5,600 IT professionals across multiple industries in mid-sized organizations across 31 countries. While it’s true cyber insurance has been playing a greater role in helping organizations improve their ability to recover from attacks, survey responses clearly indicate that ransomware poses a rising threat to government organizations.
Government Cyberattacks Increase From Previous Years
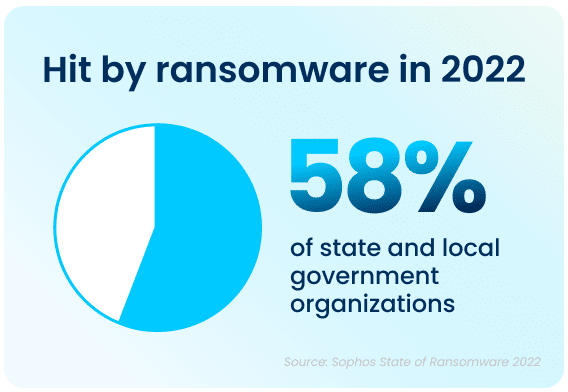
Ransomware attacks have increased significantly over the past year—58% of state and local government organizations surveyed were hit by an attack in 2021, up 70% from 2020. Bad actors are now considerably more capable of attacking organizations and executing harmful tactics at scale. The Ransomware-as-a-Service (RaaS) model is one cause of last year’s increased attacks, as the required skill level for bad actors to hamper the day-to-day operations of an organization has gone down significantly.
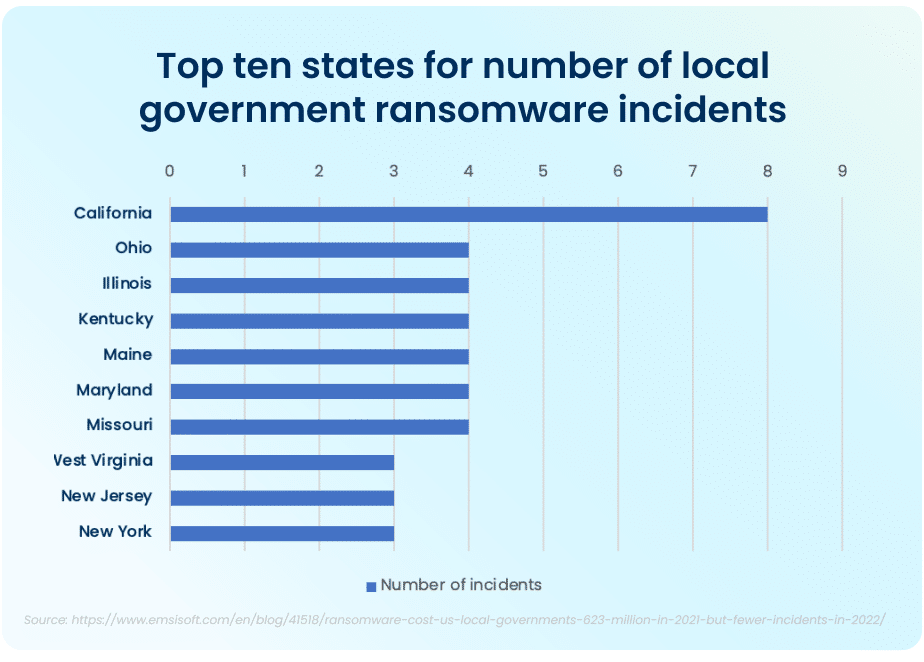
The top ten states that had to deal with the maximum amount of total ransomware attacks in the public sector in 2021 were California, who experienced the most attacks total, Ohio, Illinois, Kentucky, Maine, Maryland, and Missouri. While California took the lion’s share of attacks, with 8 major ransomware incidents, the other six states had four major incidents each.
FBI Cyber Division Survey Lists Examples of Ransomware Attacks
The Federal Bureau of Investigation (FBI) Cyber Division lists examples of several ransomware attacks that impacted state and local government organizations in their 2022 Private Industry Notification. This list contains evidence showing the impact these attacks can have on local communities.
For example, in January 2022, following a ransomware attack, a US county had to take all their systems offline and close all public locations in order to run an emergency response plan and restore all their data from backups. This action disabled all the cameras in the local county jail and deactivated automatic doors, resulting in severe safety concerns and a complete lockdown of the facility. A different county had their data—with residential and personal data—held ransom in an attack. When the ransom was not paid, all of the data was posted on the Dark Web in retaliation.
Rising Complexity of Ransomware Attacks
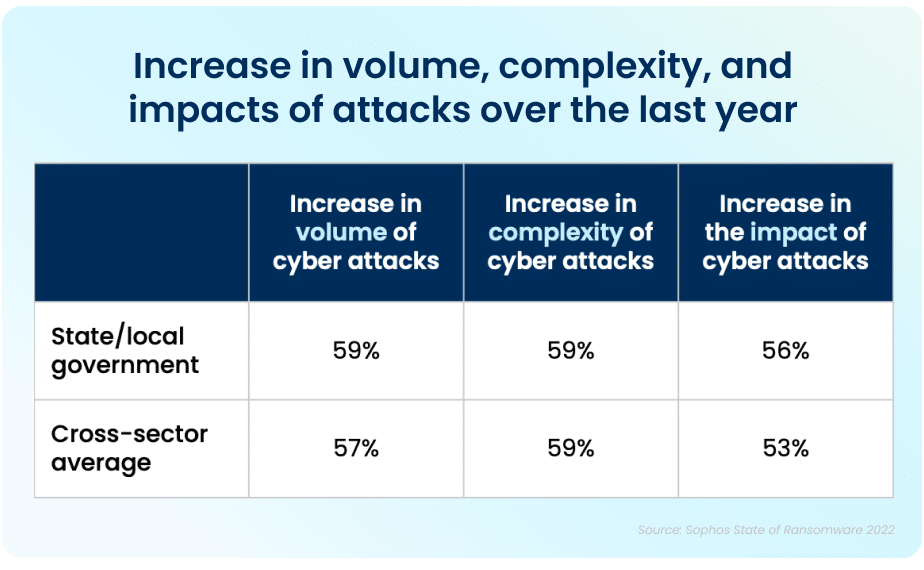
Apart from the rising prevalence of these attacks, the sheer complexity of each attack is also on an upwards trajectory. While the manufacturing and production industry reported the lowest rate of ransomware attacks, over half of all respondents reported their organization was injured by bad actors. The reality is that every organization is at high risk of cyberattack. In 2021, 59% percent of government organizations who experienced cyberattacks saw the complexity of the attacks increase, while a similar 59% saw an increase in the overall volume of cyberattacks.
Data Recovery Rates Are Improving
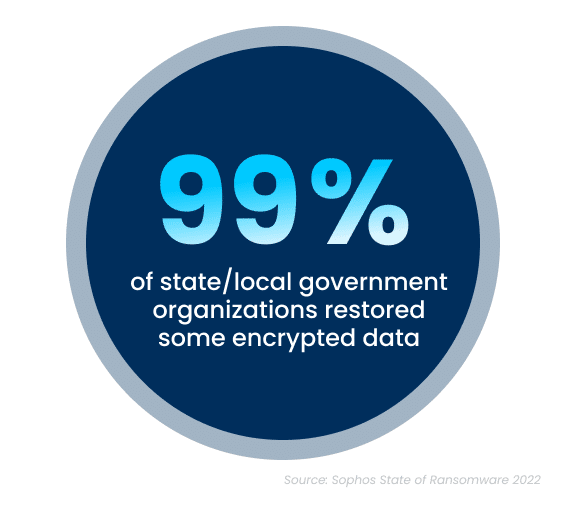
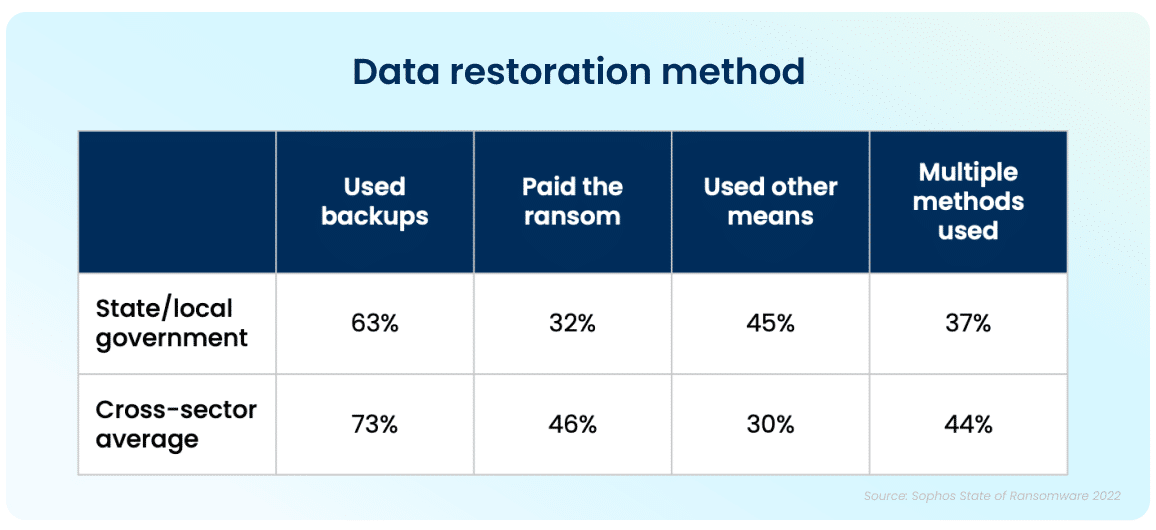
While the increase in cyberattacks paints a bleak picture, there is a silver lining to this dark cloud. Ninety-nine percent of government organizations were able to get at least some of their encrypted data back. The top method used to restore data was performed via existing backups, which were used by 63% of organizations whose data was encrypted in an attack. Unfortunately, despite the utilization of backups, 32% of the affected organizations still had to pay a ransom to ensure that more of their data was restored.
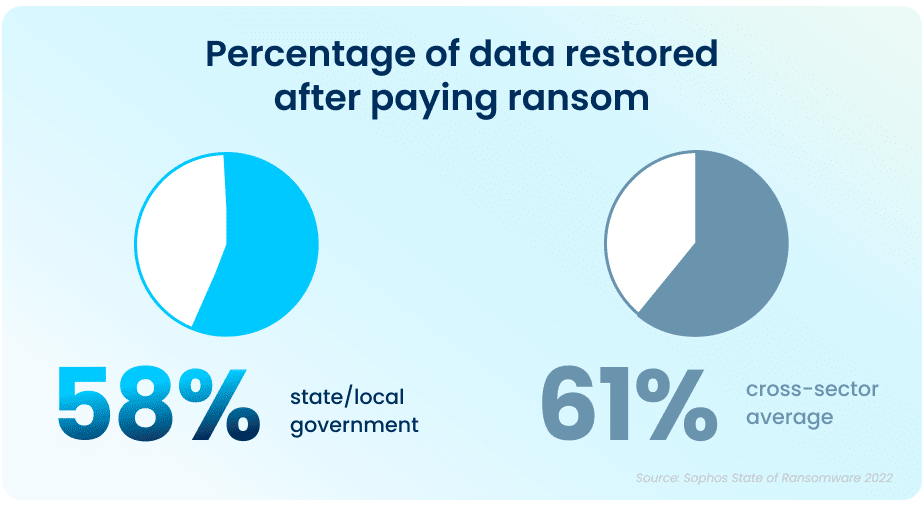
While paying a ransom typically allows organizations to get some data back, it is proving to be less effective than in years past. On average, in 2021, organizations that paid a ransom only got back 58% of their data, a considerable drop from 70% in 2020.
In April and June 2022, respectively, the states of North Carolina and Florida were the first states to prohibit state and local government organizations from paying ransoms to any bad actors. Arizona, Pennsylvania, Texas and New York are considering similar legislation. While the exact impact of this cannot be determined yet, this is expected to dissuade ransomware attacks on all organizations.
This highlights the importance of employing multiple methods to restore data—utilizing backups in particular can improve the speed of recovery and increase the amount of data that can be recovered in the event of an attack.
But It Doesn’t End There
The Sophos State of Ransomware In State and Local Government 2022 survey has revealed that ransomware continues to be an imminent threat for state and local government organizations. For many, choosing to work with an experienced partner with expertise in cybersecurity not only improves your chances of getting approved for the right amount of cyber insurance coverage, but can also ensure that companies see a higher return on investment, and improved ability to both prevent and mitigate attacks in the future. Aunalytics provides Disaster Recovery Services, which is further coupled with a comprehensive backup and archival strategy. This allows state and local government organizations like yours to remain confident so that you are prepared should you encounter a disaster event. We partner with industry leaders to replicate your critical infrastructure so you are prepared for anything.