2025 NetApp Tech ONTAP

NetApp Tech ONTAP
Crooked Ewe Brewery | South Bend, IN
Aunalytics is partnering with NetApp to bring the local tech community together to swap stories, hear updates and reconnect with peers, partners and NetApp experts. Join us for some food, drinks, fun giveaways, and hear about NetApp’s focus on Cyber Resiliency.
Gain insights into how NetApp’s relentless innovation is driving intelligent data infrastructure to meet the demands of AI and Modern IT.
Agenda:
This is a social event to meet NetApp Engineers, Sales, and Partners across your local community. Don’t miss your chance to hear first how NetApp is making your data infrastructure more seamless, more dynamic, and higher performing than ever before!
Fill out the form below to RSVP:
🗓️ Date: Thursday, November 6th, 2025
⏰ Time: 3:30pm – 5:00pm
📍 Location: Crooked Ewe Brewery, 1047 Lincolnway E, South Bend, IN 46601
Paulding-Putnam Electric Cooperative Transitions IT Infrastructure to the Cloud to Provide a Superior Customer Experience - PDF
Paulding-Putnam Electric Cooperative Transitions IT Infrastructure to the Cloud to Provide a Superior Customer Experience
Western Michigan University IT Forum Conference 2024
IT Forum Conference
Schneider Hall at Western Michigan University, Kalamazoo, MI
David Cieslak, Chief Data Scientist at Aunalytics, to speak at 2024 WMU IT Forum Conference
Aunalytics is excited to participate in the 2024 Western Michigan University IT Forum Conference in Kalamazoo, MI. David Cieslak, PhD, Chief Data Scientist at Aunalytics, will be giving a talk entitled, “Returning to the Mission of AI: Solving for Workload Imbalance“. Representatives from Aunalytics will also be on hand to discuss cybersecurity, IT, and AI topics with attendees.

Understanding the Hackers' Playbook: How to Prevent Cyberattacks and Adopt Good Practices
As increasingly sophisticated cyber threats pose risks to companies of all sizes, understanding how to prevent cyberattacks and implement good safety practices is important for any organization. This blog post discusses the common threats that companies face, effective cybersecurity strategies, and best practices for maintaining robust defenses. We’ll also explore how to foster a culture of security awareness and prepare for rapid recovery after an incident.

Understanding Common Cyberattacks
To effectively combat cyberthreats and develop smart strategies, organizations must be able to recognize common threats. One increasingly common type of attack is an opportunistic attack—attacks based on available opportunities rather than specific targets. One of the most prevalent opportunistic attacks involves exploiting known vulnerabilities—weaknesses in software or systems that, if left unpatched, can be leveraged by hackers to gain unauthorized access. For example, the Experian data breach demonstrated the dangers of neglecting known vulnerabilities. Despite being aware of the issue for weeks, Experian’s IT team failed to act, resulting in a massive compromise of personal data. This incident highlights the importance of timely patch management and proactive security measures.
Another critical threat is the compromise of business email accounts, often leading to the exploitation of platforms like Office 365. Common risk factors include the lack of Multi-Factor Authentication (MFA) and poor security practices. While MFA can significantly reduce the risk of unauthorized access, many organizations still avoid implementing it, often due to perceived inconvenience. However, the benefits of MFA far outweigh the hassle, making it a fundamental component of a strong security posture.
While technologies such as MFA are extremely effective at preventing cyberattacks, it doesn’t prevent all breaches. Phishing, though a simple, well-known concept, remains one of the most effective and damaging methods of cyberattack. Phishing emails trick recipients into divulging sensitive information or clicking on malicious links. It is all too easy for a single employee to have a brief lapse in judgement that puts an organization at risk. To combat this, phishing-resistant MFA and ongoing employee training are essential.
Key Components of an Effective Cybersecurity Strategy
To build a robust cybersecurity strategy, it’s essential to implement layered defenses and understand the key principles of security management. Phishing-resistant MFA adds an extra layer of security by requiring multiple forms of verification before granting access. This makes it significantly harder for attackers to gain unauthorized access through stolen credentials.
Additionally, understanding the shared responsibility model is crucial. Organizations must know their responsibilities and choose technology providers that align with their security needs. This includes ensuring that all security measures are covered and that responsibilities are clearly defined.
Employing established security frameworks, such as the NIST Cybersecurity Framework (CSF), can also provide a structured approach to managing and mitigating cybersecurity risks. These frameworks offer guidelines on identifying, protecting, detecting, responding to, and recovering from cybersecurity incidents.
Keeping Cybersecurity Policies Up-to-Date
Security threats are constantly evolving as hackers develop increasingly complex methods and uncover new vulnerabilities. To maintain a strong cybersecurity posture, organizations must continuously adapt their strategies—regularly reviewing and updating policies is essential. This includes conducting periodic assessments and audits to ensure that policies remain effective and relevant. It is also beneficial to regularly test and refine response plans by conducting tabletop exercises to simulate cybersecurity incidents. These exercises help organizations prepare for real-world scenarios and improve their incident response strategies.
As tactics evolve and new vulnerabilities are uncovered, organizations must stay informed of the latest security news and intelligence. This can include gathering threat intelligence from partners and industry sources, and staying informed through news articles, social media, and threat intelligence feeds. Additionally, engaging in a crowdsourced approach to security allows organizations to tap into a broader pool of knowledge and expertise. Participating in cybersecurity forums and collaborating with external security experts can take this knowledge a step further and helps organizations learn how to proactively address potential risks.
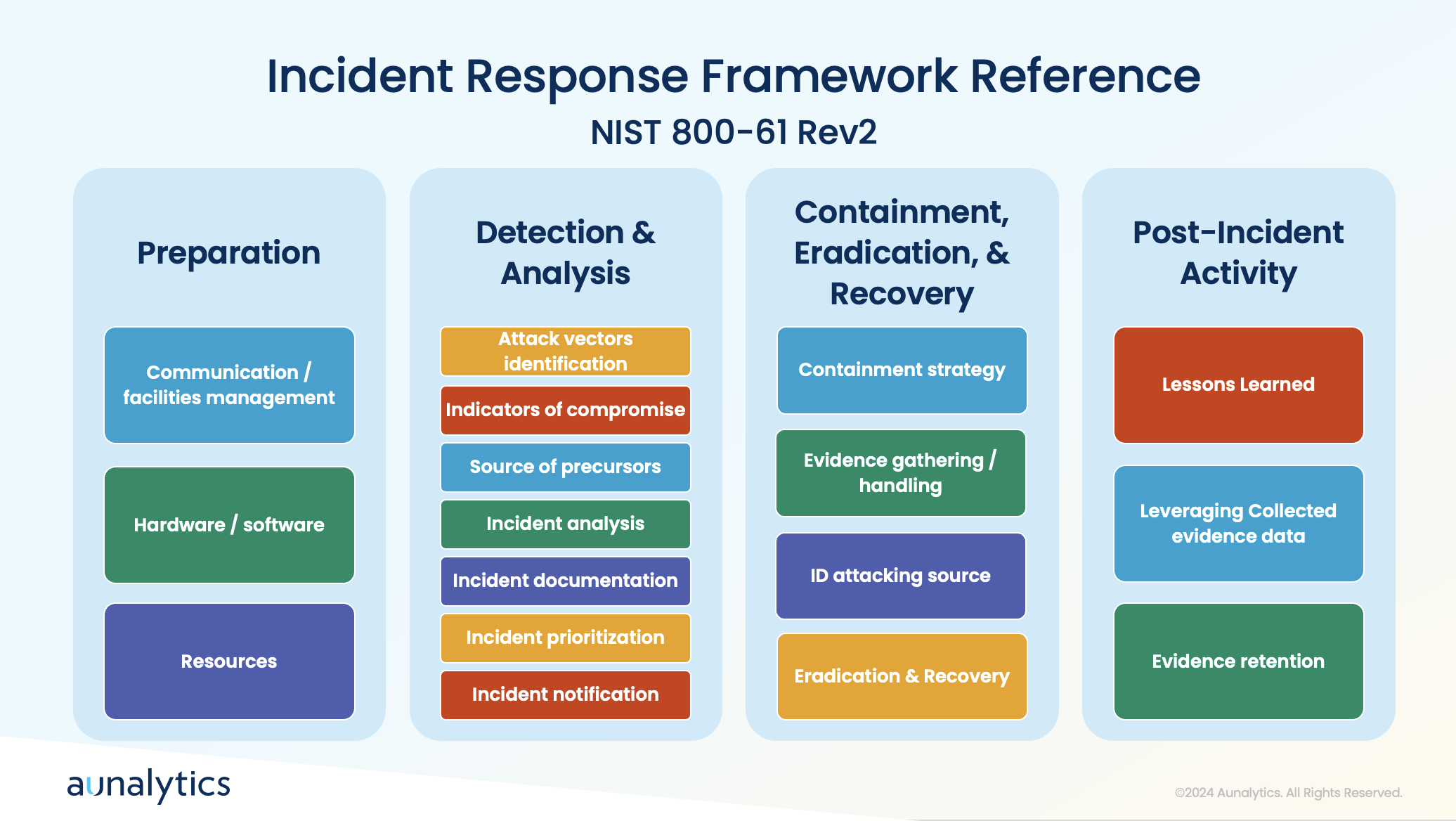
Best Practices for Incident Response
While putting safeguards in place to prevent cyberattacks from occurring is imperative, it is also equally important to prepare your organization to respond appropriately when an incident does occur. During a cyberattack, it’s crucial to have tools in place to detect anomalies and communicate effectively. Quick actions include containing the incident by taking affected systems offline, blocking access to malicious platforms, and assessing the scope of the breach.
A clear communication plan and understanding of the attack’s attribution are essential for effective recovery. Preparation involves establishing processes for detection, analysis, containment, eradication, and recovery, followed by post-incident activities to improve future responses.
Employee Training and Awareness

To ensure that all areas of a company take an active role to prevent cyberattacks, it’s crucial to foster a strong security culture. Unfortunately, employees often make mistakes that lead to breaches, such as falling for phishing schemes or responding to solicitation calls. Educating staff about the tactics used by attackers, such as impersonation and social engineering, can help prevent these errors.
Therefore, it is crucial to ensure that all employees have access to cybersecurity training—this training covers the basics of recognizing bad actors and avoiding common traps.
Tailoring training to specific roles and conducting phishing email simulations can enhance employees’ ability to identify and respond to threats. Creating a culture of cybersecurity awareness involves emphasizing the importance of security to employees and their families. This helps instill a sense of personal responsibility for maintaining security practices.
For IT and cybersecurity professionals, it is greatly beneficial to focus on developing a strong understanding of network engineering, including routing, switching, and firewall management. Additionally, the ability to visualize and comprehend data flows and security information is crucial for effective security management. IT teams must avoid cutting corners and ensure robust security measures are in place. They play a critical role in enforcing security policies and preventing breaches, making their diligence essential.
Conclusion
Understanding the tactics used by attackers and implementing robust preventive measures is key to safeguarding your organization. By adopting best practices such as phishing-resistant MFA, regularly updating policies, leveraging threat intelligence, and training employees effectively, companies can significantly reduce their risk of cyberattacks. Additionally, having a well-defined incident response plan and fostering a culture of security awareness ensures preparedness for any potential breaches. By following these guidelines, organizations can better protect their data and maintain a strong defense against cyber threats.

Partnering with Aunalytics ensures your data privacy and security through a comprehensive approach that includes advanced risk assessments, phishing-resistant Multi-Factor Authentication (MFA), and continuous updates to align with industry standards like the NIST Cybersecurity Framework. Our expert team provides 24/7 monitoring and rapid threat response, leveraging cutting-edge technology and threat intelligence to preemptively address risks. With Aunalytics, you benefit from top-tier protective measures and a commitment to adapting strategies to emerging threats, ensuring your data remains secure and confidential.
2024 Ohio Information Security Conference
2024 Ohio Information Security Conference
Sinclair Conference Center, Dayton, OH
Aunalytics to Attend and Speak at the 2024 Ohio Information Security Conference
Aunalytics is excited to attend the 2024 Ohio Information Security Conference presented by Technology First in Dayton, OH as a Gold Sponsor. The Aunalytics team is excited to connect with fellow IT professionals to discuss security and innovation in the technology field. Kerry Vickers, CISO of Aunalytics will be joining Max Aulakh, President and Founder of Ignyte, to present “Incident Response Live!” —a tabletop group exercise from 1:30-2:30pm.

2023 misecCON
2023 misecCON
Radisson Hotel Lansing at the Capital, Lansing, MI
Aunalytics Is Excited to Attend the 2023 MisecCON as a Bronze Sponsor
Aunalytics is excited to attend 2023 misecCON in Lansing, MI. The Aunalytics team is excited to connect with fellow security experts and discuss new developments and innovation in the field.

2023 Technology First Taste of IT Conference
2023 Technology First Taste of IT Conference
Sinclair Conference Center, Dayton, OH
Aunalytics Is Excited to Attend the 2023 Technology First Taste of IT Conference
Aunalytics is excited to attend the 2023 Technology First Taste of IT Conference in Dayton, OH as a Gold Sponsor. The Aunalytics team is excited to connect with fellow IT professionals to discuss security and innovation in the technology field.

2023 Columbus Connect Networking Event
2023 Columbus Connect Networking Event
Columbus Zoo - Heart of Africa Event Center, Columbus, OH
Aunalytics Is Excited to Attend the 2023 Columbus Connect Networking Event
Aunalytics is excited to attend the 2023 Columbus Connect Networking Event, sponsored by its technology partner, Cologix. The Aunalytics team is excited to connect with fellow IT professionals to discuss security and innovation in the technology field.

2023 IBA Security & Technology Conference
IBA Security & Technology Conference
Renaissance Indianapolis North Hotel, Carmel, IN
Aunalytics Is Proud to Be a Breakfast Sponsor at the 2023 IBA Security & Technology Conference
Aunalytics is excited to attend the Indiana Bankers Association Security & Technology Conference in Carmel, IN. Aunalytics is participating as a Breakfast Sponsor and our team is excited to connect with fellow IT professionals to discuss security and innovation in the technology field.